Chp 6 infrastructure- the backbone of e-commerce tech
-
Upload
cheqala5626 -
Category
Business
-
view
3.996 -
download
0
description
Transcript of Chp 6 infrastructure- the backbone of e-commerce tech

CHAPTER 6
INFRASTRUCTURE: THE BACKBONE OF E-COMMERCE TECHNOLOGY
DIPLOMA IN INTERNATIONAL BUSINESS(BUS2513)

2
Requirements for Successful Service
Technology
Regulation Market
Standards
Can it be built?
Will it sell?Is it allowed?
Will it inter-operate?

3
Years to reach 50M users:
0
30
60
90
120
‘22 ‘30 ‘38 ‘46 ‘54 ‘62 ‘70 ‘78 ‘86 ‘94 ‘02
Us
ers
(M
illio
ns
)
Radio TVCable Internet
Source: Morgan Stanley
Radio = 38TV = 13
Cable = 10
Internet = 5
Industry & Society: Penetration Rates

4
Year
MIPS
Giga PC
10G PC
Tera PC
100G PC
Doubling every 15 months
Doubling every 2 years
From: Raj Reddy- The Global Village
The Heart of the Matter: The Growth of Computers

5
Storage Performance

6
Optical Fiber: Promise & Performance
10 Gb/s
100 Gb/s
1,000Gb/s
1 Gb/s
1978 Projection1978 Projection
1980 Projection1980 Projection
1987 Projection1987 Projection
1995 1995 ProjectionProjection
1983 Projection1983 Projection
Bell Labs
Gilder’s Law – Optical speeds doubling in ~ 9 months

7
Software Challenges in Intelligent Data Processing
38
User Decision Support Demandvs. Processor speed
1
10
100
1996 1997 1998 1999 2000
CPU speed2X / 18 months
Database demand:2X / 9-12 months
Database-Proc.Performance Gap:“Greg’s Law”
“Moore’s Law”

8
What Makes the Internet tick? The Internet runs on 3 things:
Boundaries Limits of Responsibilities Inside the core, is like a black box (“The Cloud”)
Standards (protocols) for data-centric design Expectations of how things should work together
Layering Robustness Principle
"Be liberal in what you accept, and conservative in what you send.“ – Jon Postel
Resiliency – distributed architecture Limits Monopolies NO ONE OWNS THE INTERNET
Trust Addressing schemes and registration End-to-end design

9
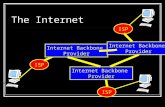
What is the Internet?
The global (public) network built from hundreds and thousands of internetworking independent networks.
No single entity “runs” the Internet
Operates on standards Built on a modified
hierarchical structure Packet Switching
Tier 1
a.k.a. Backbone Providers
Tier 2
Users
• There are often more layers• There can be interconnections other
than at a backbone

10
Applications vs. Networking Parameters

11
Internet is built on trust:
Registration (databases) are believed because people think they are correct Domain Name System
Handles names for humans vs. binary for machines
Root names are the last “.???”, .com, .edu, .org, .mil, .ca, .tv
Just 13 root servers in the world Many copies made for practical purposes
Borders define responsibilities

12

13
Standards and Regulation Many bodies, sometimes with overlap
IETF (within IAB) handles the engineering of the network
W3C handles web standards such as html, xml, etc. IEEE handles some standards
Requests for Comments (RFCs) are how things get standardized Draft is circulated Modified, debated, etc. (many versions often) Becomes a standard by vote.
Companies often try and tilt emerging standards

14
Client/Server Computing on the InternetClient/Server Computing on the Internet
The Internet
Client computers running Web browser and other software can access an array of services on servers over the Internet. These services may all run on a single server or on multiple specialized servers.

15
Issues in the Internet
Scalability Internet is growing* at 100-300% Running out of IP addresses –
Long term solution: IPv6 128 bit addresses (millions per square meter)
Protocols and equipment are straining Security
Distributed Denial of Service – example of an attack
Viruses Spam Privacy
Quality of Service Voice

Online Business Networks

17
Business Networking
Traditionally, businesses would form networking entities in order to perform business activities
Networking is an important component of any job search, and many professionals have participated in some form of networking during their careers.

18
Business networking
Advantages of networking Improved supplier & distributor relationships Enhanced procurement & distribution
activities Additional market coverage Discovery of new resources
Traditional business networking involved: Telephone calls Faxes Face-to-face meetings

19
Online Business Networking
Cybernetworks – online web community Virtual space Community of members sharing same interest Growing in attention “Word-of-mouth” prevalent
Definition An online web community or online mobile
community may be defined as a virtual space (social media) created by members, using appropriate social software provided and managed by the owner of the service, where all participants have at least one purpose to consume, generate and interact with content (user generated content) or interact with other members (social networking).

20
Technologies and Tools for Communication and E-BusinessTechnologies and Tools for Communication and E-Business
Online Business NetworksOnline Business Networks
• E-mail, chat, instant messaging, and electronic discussions (Yahoo messenger, IRC, videoconferencing)
• Groupware and electronic conferencing (UUM portal)
• Internet telephony (Skype)
• Virtual private networks

Wireless Environment

22
Definition and Description The term wireless is normally used to
refer to any type of electrical or electronic operation which is accomplished without the use of a "hard wired" connection.
Wireless communication is the transfer of information over a distance without the use of electrical conductors or "wires". The distances involved may be short (a few
meters as in television remote control) or very long (thousands or even millions of kilometers for radio communications). When the context is clear the term is often simply shortened to "wireless".
Wireless communications is generally considered to be a branch of telecommunications.

23
Examples of Wireless Devices
It encompasses cellular telephones, personal digital assistants (PDAs), and wireless networking. Other examples of wireless technology include GPS units, garage door openers and or garage doors, wireless computer mice and keyboards, satellite television and cordless telephones.

24
Wireless Form
Wireless communication may be via: radio frequency communication, microwave communication, for example long-
range line-of-sight via highly directional antennas, or short-range communication, or
infrared (IR) short-range communication, for example from remote controls or via IRDA,
Applications may involve point-to-point communication, point-to-multipoint communication, broadcasting , cellular networks and other wireless networks.

25
• Wireless devices (PDAs, BlackBerry, smart phones)
• Cellular systems• Cellular network standards and generations (GSM, CDMA)
• Cellular generations (SMS, 3G, 2.5G)
• Mobile wireless standards for Web access (WAP, I-mode)
• Wireless computer networks and Internet access• Bluetooth (PANs)
• Wi-Fi (access points)
• Wi-Fi and wireless Internet access (hotspots)
• WiMax
• Broadband cellular wireless (EV-DO)
The Wireless Revolution

26
Spectrum
Frequency affects
Capacity Bandwidth
Range Interference
and Line of Sight Requirements
Protocols and Technology
ISM Bands are kept free for Industrial, Scientific, and Medical Applications, e.g., 2.4 GHz

27
Applications of wireless technology
Security systems Wireless technology may supplement or
replace hard wired implementations in security systems for homes or office buildings.
The operations that are required (e.g., detecting whether a door or window is open or closed) may be implemented with the use of hard wired sensors or they may be implemented with the use of wireless sensors which are also equipped with a wireless transmitter (e.g., infrared, radio frequency, etc.) to transmit the information concerning the current state of the door or window.
Car Security Remote

28
Applications of wireless technology
Remote control Some televisions were previously
manufactured with hard wired remote controls which plugged in to a receptacle or jack in the television whereas more modern televisions use wireless (generally infrared) remote control units.
Radio Remote Control – Similar to the TV remote control
DVD/VCD Player Remote Control Fan Remote Control

29
Applications of wireless technology
Cellular telephones Perhaps the best known example of wireless
technology is the cellular telephone. These instruments use radio waves to
enable the operator to make phone calls from many locations world-wide.
They can be used anywhere that there is a cellular telephone site to house the equipment that is required to transmit and receive the signal that is used to transfer both voice and data to and from these instruments.

30
• RFID and wireless sensor networks
• Radio frequency identification (RFID)
• Powerful technology for tracking goods in a supply chain using radio signals
• Reduction in cost of RFID tags now making the technology viable for many firms
• Wireless sensor networks
• Can be used to monitor building security, detect hazardous substances in the air, or monitor environmental changes, traffic, or military activity
• Require low-power, long-lasting batteries and ability to endure in the field without maintenance
The Wireless Revolution

31
How RFID WorksHow RFID Works
The Wireless Revolution
RFID uses low-powered radio transmitters to read data stored in a tag at distances ranging from 1 inch to 100 feet. The reader captures the data from the tag and sends them over a network to a host computer for processing.

32
Why use wireless?
The following situations justify the use of wireless technology: To span a distance beyond the capabilities of
typical cabling, To avoid obstacles such as physical
structures, EMI, or RFI, To provide a backup communications link in
case of normal network failure, To link portable or temporary workstations, To overcome situations where normal cabling
is difficult or financially impractical, or To remotely connect mobile users or
networks.

33
Wireless Device Connection
IrDA-Control 72 kbit/s IrDA-SIR 115.2 kbit/s 802.15.4 (2.4 GHz) 250 kbit/s Bluetooth 1.1 1000 kbit/s Bluetooth 2.0+EDR 3000 kbit/s IrDA-FIR 4000 kbit/s IrDA-VFIR 16,000
kbit/s WUSB-UWB 480,000 kbit/s

34
Wireless Local Area Network
A wireless LAN or WLAN is a wireless local area network, which is the linking of two or more computers without using wires. WLAN utilizes spread-spectrum or OFDM modulation technology based on radio waves to enable communication between devices in a limited area, also known as the basic service set.
This gives users the mobility to move around within a broad coverage area and still be connected to the network.

35

36
Wireless Networking Standards
802.11 legacy 0.125 2.0 Mbit/s RONJA 10.0 Mbit/s 802.11b DSSS 0.125 11.0
Mbit/s 802.11b+ 44.0 Mbit/s 802.11a 0.75 54.0 Mbit/s 802.11g OFDM 0.125 54.0 Mbit/s 802.16 (WiMAX) 70.0 Mbit/s 802.11gt DSSS 0.125 108 Mbit/s 802.11n 248 Mbit/s

37
Benefits of WLAN Convenience: The wireless nature of such
networks allows users to access network resources from nearly any convenient location within their primary networking environment (home or office). With the increasing saturation of laptop-style computers, this is particularly relevant.
Mobility: With the emergence of public wireless networks, users can access the internet even outside their normal work environment. Most chain coffee shops, for example, offer their customers a wireless connection to the internet at little or no cost.

38
Benefits of WLAN
Productivity: Users connected to a wireless network can maintain a nearly constant affiliation with their desired network as they move from place to place. For a business, this implies that an employee can potentially be more productive as his or her work can be accomplished from any convenient location.
Deployment: Initial setup of an infrastructure-based wireless network requires little more than a single access point. Wired networks, on the other hand, have the additional cost and complexity of actual physical cables being run to numerous locations (which can even be impossible for hard-to-reach locations within a building).

39
Benefits of WLAN
Expandability: Wireless networks can serve a suddenly-increased number of clients with the existing equipment. In a wired network, additional clients would require additional wiring.
Cost: Wireless networking hardware is at worst a modest increase from wired counterparts. This potentially increased cost is almost always more than outweighed by the savings in cost and labor associated to running physical cables.

40
Weaknesses of WLAN
Security: Wireless LAN transceivers are designed to serve computers throughout a structure with uninterrupted service using radio frequencies. What this means is that not only can the wireless packets be intercepted by a nearby adversary's poorly-equipped computer, but more importantly, a user willing to spend a small amount of money on a good quality antenna can pick up packets at a remarkable distance; perhaps hundreds of times the radius as the typical user. To combat this, wireless networks users usually choose to utilize various encryption technologies available such as Wi-Fi Protected Access (WPA).

41
Weaknesses of WLAN
Range: The typical range of a common 802.11g network with standard equipment is on the order of tens of meters. OK for home, NOT OK in larger structures. To obtain additional range, repeaters or additional access points will have to be purchased.
Reliability: Wireless networking signals are subject to a wide variety of interference, as well as complex propagation effects (such as multipath, or especially in this case Rician fading) that are beyond the control of the network administrator.

42
Weaknesses of WLAN
Speed: The speed on most wireless networks (typically 1-108 Mbit/s) is reasonably slow compared to the slowest common wired networks (100 Mbit/s up to several Gbit/s). There are also performance issues caused by TCP and its built-in congestion avoidance. In most environments, a wireless network running at its slowest speed is still faster than the internet connection serving it in the first place. However, in specialized environments, higher throughput through a wired network might be necessary. Newer standards such as 802.11n are addressing this limitation and will support peak throughputs in the range of 100-200 Mbit/s.

Streaming Media

44
What is it?
Streaming media enables real-time or on-demand access to audio, video, and multimedia content via the Internet or an intranet.
Streaming media is transmitted by a specialized media server application, and is processed and played back by a client player application, as it is received, leaving behind no residual copy of the content on the receiving device.

45
Characteristics of Streaming Media
1. Streaming media technology enables real-time or on-demand access to audio, video, and multimedia content via the Internet or an intranet. Streaming technology enables the near real-
time transmission of events recorded in video and/oraudio, as they happen—sometimes called “Live-Live,” and commonly known as Webcasting.
Streaming technology also makes it possible to conveniently distribute pre-recorded/pre-edited media on-demand.
In other words, media that is stored and published on the Web in streaming formats can be made available for access at any time.

46
Characteristics of Streaming Media
2. Streaming media is transmitted by a media server application, and is processed and played back by a client player application, as it is received. A client application, known as player, can start
playing back streaming media as soon as enough data has been received—without having to wait for the entire file to have arrived.
As data is transferred, it is temporarily stored in a buffer until enough data has accumulated to be properly assembled into the next sequence of the media stream.

47
Characteristics of Streaming Media
3. A streamed file is received, processed, and played simultaneously and immediately, leaving behind no residual copy of the content on the receiving device. An important advantage of streaming media
(unlike either traditional or progressive download) technology is the copyright protection it provides.
No copy of the content is left on the receiving device.
Therefore, the recipient can neither alter nor redistribute the content in an unauthorised manner.

48
Uses of Streaming Media
The three most common ways enterprises use streaming are for: corporate communications, electronic learning, and sales and marketing.

49
Examples of Streaming Media
Enterprise customers should consider using streaming technology to: Send e-broadcasts across their corporations Give remote presentations to employees,
customers, and partners Deliver end-to-end training to the sales
force or retail locations Enhance professional development and
communicate HR policies Conduct pre-sales demos Provide customer service

50
Advantages of Streaming Media No waiting for complete downloads—well, not
“much” waiting, anyway. Streamed files are not written to disk—they
are processed and played as they are received, then discarded, leaving no residual copy of the content on the receiving device, and thereby alleviating copyright concerns.
Streaming is capable of conveying live events around the globe in near real time.
Supports interactivity, allowing content to be experienced in a non-linear manner. Video-on-demand, for example, can be chapterised, allowing users to jump to desired portions.
Streaming content is an excellent way to enhance otherwise static Web sites.

51
How does it work?

52
Main Streaming Media
Architecture Native Formats / Codecs
Streaming Media File Attention
QuickTime QuickTime .mov, .qt, .qti
RealMedia RealMedia .rm, .rmv
Windows Media
Advanced Streaming Format or Windows Media Video/Audio
.asf, .wmv, .wma

53
Unicasting

54
Multicasting

Biometric Technologies

56
Evolving Definition
Biometrics (ancient Greek: bios ="life", metron ="measure") refers to two very different fields of study and application. The first, which is the older and is used in biological studies, including forestry, is the collection, synthesis, analysis and management of quantitative data on biological communities such as forests. Biometrics in reference to biological sciences has been studied and applied for several generations and is somewhat simply viewed as "biological statistics."
More recently and incongruently, the term's meaning has been broadened to include the study of methods for uniquely recognizing humans based upon one or more intrinsic physical or behavioral traits.

57
Biometrics are used to identify the identity of an input sample when compared to a template, used in cases to identify specific people by certain characteristics.
possession-based: using one specific "token" such as a security tag or a card
knowledge-based :the use of a code or password. Standard validation systems often use multiple
inputs of samples for sufficient validation, such as particular characteristics of the sample.
This intends to enhance security as multiple different samples are required such as security tags and codes and sample dimensions.

58
Characteristics of Biometrics Physical features, such as face, fingerprint,
iris, retina, hand, or behavioral features, such as signature, voice, gait, must fulfill a certain criteria to qualify for use in identification.
They must be unique, universal, acceptable, collectable and convenient to the person, in addition, to reliability at identification performance and circumvention.
However, most importantly, permanence is a key feature for biometrics. They must retain all the above features in particular the uniqueness unchanged, or acceptably changed, over the lifetime of the individual.

59
Types of Biometrics
Biometric characteristics can be divided in two main classes: physiological are related to the shape of
the body. The oldest traits, that have been used for more than 100 years, are fingerprints. Other examples are face recognition, hand geometry and iris recognition.
behavioral are related to the behavior of a person. The first characteristic to be used, still widely used today, is the signature. More modern approaches are the study of keystroke dynamics and of voice.

60
Common Human Biometrics

61
Things to Note
Strictly speaking, voice is also a physiological trait because every person has a different pitch, but voice recognition is mainly based on the study of the way a person speaks, commonly classified as behavioral.
Other biometric strategies are being developed such as those based on gait (way of walking), retina, hand veins, ear recognition, facial thermogram, DNA, odor and palm prints.

62
Measurement It is possible to understand if a human
characteristic can be used for biometrics in terms of the following parameters: Uniqueness is how well the biometric
separates individually from another. Permanence measures how well a biometric
resists aging. Collectability ease of acquisition for
measurement. Performance accuracy, speed, and
robustness of technology used. Acceptability degree of approval of a
technology. Circumvention ease of use of a substitute.

63
Biometric System

64
Biometric System Explanation The main operations a system can perform are enrollment
and test. During the enrollment, biometric information from an individual is stored. During the test, biometric information is detected and compared with the stored information. Note that it is crucial that storage and retrieval of such systems themselves be secure if the biometric system is be robust. The first block (sensor) is the interface between the real world and our system; it has to acquire all the necessary data. Most of the times it is an image acquisition system, but it can change according to the characteristics desired. The second block performs all the necessary pre-processing: it has to remove artifacts from the sensor, to enhance the input (e.g. removing background noise), to use some kind of normalization, etc. In the third block features needed are extracted. This step is an important step as the correct features need to be extracted and the optimal way. A vector of numbers or an image with particular properties is used to create a template. A template is a synthesis of all the characteristics extracted from the source, in the optimal size to allow for adequate identifiability.

65
Biometric System Function
A biometric system can provide the following two functions: Verification A pre-stored template is
matched against a sample directly, e.g. a card or known database entry.
Identification Identifying from all the templates which one is the closest match to the input sample.

Business Avatars

67
Definition
An avatar (abbreviations include AV, ava, avie, avy, avi, avvie, avis, avies, avii, and avvy) is computer user's representation of himself or herself, whether in the form of a three-dimensional model used in computer games, a two-dimensional icon (picture) used on Internet forums and other communities, or a text construct found on early systems such as MUDs.
The term "avatar" can also refer to the personality connected with the screen name, or handle, of an Internet user.

68
Used in computer games Ultima IV (1985) - Avatar was the
player's visual on-screen in-game persona which could be customised in appearance.
Wide use in Forums Avatars on Internet forums serve the
purpose of representing users and their actions, personalizing their contributions to the forum, and may represent different parts of their persona, beliefs, interests or social status in the forum.

69
Examples of Avatars

70
Business
In business, avatars are used to represent the ‘heart’ of the business.
Similar to business icons used to reflect the company. Can you name any? Shell?

Web Browsers

72
APLIKASI INTERNETAPLIKASI INTERNET
• Terdapat dua jenis pelayar web iaitu
1. Pelayar web yang berunsurkan teks
• Pelayar web yang berunsurkan teks seperti Lynx merupakan versi pelayar web yang lama. Lynx beroperasi dalam mod teks sahaja.
• Pengguna Lynx hanya dapat belayar di Internet dengan memilih perkataan pada skrin dengan menggunakan kekunci anak panah dan kekunci ENTER pada papan kekunci komputer.

73
APLIKASI INTERNETAPLIKASI INTERNET
2. Pelayar web yang berunsurkan grafik
• Pelayar web yang berunsurkan grafik seperti Internet Explorer dan Netscape merupakan versi pelayar web yang lebih mudah, baru dan canggih.
• Teks, imej, aplikasi video dan audio dipaparkan secara grafik dan dapat diperoleh dengan memuat turun ke komputer pengguna.

74
Description
A web browser is a software application that enables a user to display and interact with text, images, videos, music and other information typically located on a Web page at a website on the World Wide Web or a local area network.
Text and images on a Web page can contain hyperlinks to other Web pages at the same or different website.
Web browsers allow a user to quickly and easily access information provided on many Web pages at many websites by traversing these links.
Web browsers format HTML information for display, so the appearance of a Web page may differ between browsers.

75
Historically important browsers
In order of release: WorldWideWeb, February 26, 1991 Erwise, April 1992 ViolaWWW, May 1992, see Erwise WWW - The Libwww Line-Mode Browser, before
February 11, 1991 Mosaic, April 22, 1993 Netscape Navigator and Netscape Communicator,
October 13, 1994 Internet Explorer (including
Internet Explorer for Mac and Internet Explorer for UNIX), August 1995, see History of Internet Explorer
Opera, 1996, see History of the Opera Internet suite
Mozilla Firefox, 2004

76
Popular Browsers and Market Share

77
Protocols and Standards
Web browsers communicate with Web servers primarily using HTTP (hypertext transfer protocol) to fetch webpages.
HTTP allows Web browsers to submit information to Web servers as well as fetch Web pages from them.
The most commonly used HTTP is HTTP/1.1, which is fully defined in RFC 2616.
HTTP/1.1 has its own required standards that Internet Explorer does not fully support, but most other current-generation Web browsers do.

78
Pages are located by means of a URL (uniform resource locator, RFC 1738 ), which is treated as an address, beginning with http: for HTTP access.
Many browsers also support a variety of other URL types and their corresponding protocols, such as gopher: for Gopher (a hierarchical hyperlinking protocol), ftp: for FTP (file transfer protocol), rtsp: for RTSP (real-time streaming protocol), and https: for HTTPS (an SSL encrypted version of HTTP).

79
The file format for a Web page is usually HTML (hyper-text markup language) and is identified in the HTTP protocol using a MIME content type.
Most browsers natively support a variety of formats in addition to HTML, such as the JPEG, PNG and GIF image formats, and can be extended to support more through the use of plugins.
The combination of HTTP content type and URL protocol specification allows Web page designers to embed images, animations, video, sound, and streaming media into a Web page, or to make them accessible through the Web page.

80
APLIKASI INTERNETAPLIKASI INTERNET
Merupakan pengimbas web popular yang dibangunkan oleh Microsoft Corporation.
Antara muka yang menarik dan mudah digunakan untuk memaparkan halaman web.
Antaramuka pengimbas ini terbahagi kepada empat bahagian utama iaitu Pull Down Menu, Navigation Button, Address Bar dan Paparan Web.
Internet Explorer

81
APLIKASI INTERNETAPLIKASI INTERNET
Tetingkap Internet Explorer

Business Community Collaboration

83
Business Community Collaboration
Organisations working together to achieve a common goal or a set of objectives.
Three main types of business communities: Business Organisation Government Agencies Consumer Group

84
E-Business – EC Organizations
Brick-and-mortar (or old-economy) refer to pure physical organizations (corporations).
Virtual (or pure-play) organizations are companies that are engaged only in EC .
Click-and-mortar (or click-and-brick) organizations are those that conduct some e-commerce activities, yet their primary business is done in the physical world.
E-commerce describes the process of buying, selling, transferring, or exchanging products, services, and/or information via computer networks, including the Internet. E-business refers to a broader definition of e-commerce, not just the buying and selling of goods and services, but also servicing customers, collaborating with business partners, conducting e-learning, and processing electronic transactions.

85
Collaboration Types
Transactions can be done between various parties.
Business-to-business (B2B): Both the sellers and the buyers are business organizations.
Collaborative commerce (c-commerce): In c-commerce, business partners collaborate electronically.
Business-to-consumers (B2C): The sellers are organizations, and the buyers are individuals.
Consumers-to-businesses (C2B): Consumers make known a particular need for a product or service, and suppliers compete to provide it.

86
Collaboration Types (Continued)
Transactions can be done between various parties.
Consumer-to-consumer (C2C): Individuals sell products or services to other individuals.
Intrabusiness (intraorganizational) commerce: An organization uses EC internally to improve its operations. A special case is known as B2E (business to its employees)
Government-to-citizens (G2C): A government provides services to its citizens via EC technologies.
Mobile commerce (m-commerce): When e-commerce is done in a wireless environment.

87
Business-To-Business – B2B
Sell-Side Marketplaces: organizations attempt to sell their products or services to other organizations electronically, from their own private e-marketplace. This model is similar to the B2C model in which the buyer is expected to come to the seller’s site and place an order.
Buy-Side Marketplaces: organizations attempt to buy needed products or services from other organizations electronically, usually from their own private e-marketplace. One buy-side model is a reverse auction. Here, a company that wants to buy items places a request for quotation (RFQ) on its Web site, or in a third-party bidding marketplace.
In B2B applications, the buyers, sellers, and transactions involve only organizations. It covers a broad spectrum of applications that enable an enterprise to form electronic relationships with its distributors, resellers, suppliers, customers, and other partners.

88
Business-To-Business – B2B (Continued)
E-procurement. Purchasing by using electronic support is referred to as e-procurement. In addition to reverse auctions e-procurement uses other mechanism. Two popular ones are group purchasing and desktop purchasing.
Group purchasing the requirements of many buyers are aggregated so that they total a large volume, and thus merit more seller attention. Once buyers’ orders are aggregated, they can be placed on a reverse auction, and a volume discount can be negotiated.
Desktop purchasing. In this variation of e-procurement, suppliers’ catalogs are aggregated into an internal master catalog on the buyer’s server, so that the company’s purchasing agents can shop more conveniently. Desktop purchasing is most suitable for maintenance, replacement, and operations (MRO) indirect items, such as office supplies.

89
Business-To-Business – B2B (Continued)
Electronic Exchanges are E-marketplaces in which there are many sellers and many buyers.
Vertical distributors for direct materials: These are B2B marketplaces where direct materials (materials that are inputs to manufacturing) are traded in an environment of long-term relationship, known as systematic sourcing.
Vertical exchanges for indirect materials: Here indirect materials in one industry are purchased on an “as-needed” basis (called spot sourcing). Buyers and sellers may not know each other. In such vertical exchanges, prices are continually changing, based on the matching of supply and demand.
Horizontal distributors: These are “many-to-many” e-marketplaces for indirect (MRO) materials, such as office supplies, used by any industry. Prices are fixed or negotiated in this systematic sourcing-type exchange.
Functional exchanges: Here, needed services such as temporary help or extra space are traded on an “as-needed” basis (spot sourcing). Prices are dynamic, and they vary depending on supply and demand.

90
Business-To-Consumer – B2C
Electronic retailing (e-tailing) is the direct sale of products through electronic storefronts or electronic malls, usually designed around an electronic catalog format and/or auctions.
Electronic Storefronts. Hundreds of thousands of solo storefronts can be found on the Internet, each with its own Internet name and EC portal, such as Home Depot, The Sharper Image, or Wal-Mart.
Electronic mall, also known as a cybermall or e-mall, is a collection of individual shops under one Internet address. The basic idea of an electronic mall is the same as that of a regular shopping mall—to provide a one-stop shopping place that offers many products and services.
For generations home shopping from catalogs has flourished, and television shopping channels have attracted millions of shoppers. However, these methods have drawbacks: Both methods can be expensive; paper catalogs are sometimes not up-to-date; and television shopping is limited to what is shown on the screen at any given time.

91
Service Industries – B2C
Electronic banking, also known as cyberbanking includes various banking activities conducted from home or a business instead of at a physical bank
International and Multiple-Currency Banking. International banking and the ability to handle trading in multiple currencies, transfers of electronic funds and electronic letters of credit are critical for international trade.
Online Securities Trading can be placed from anywhere, any time. Investors can find a considerable amount of information regarding a specific company or in a mutual fund.
Online Job Market. The Internet offers a perfect environment for job seekers and for companies searching for employees.
Travel Services. The Internet is an ideal place to plan, explore, and arrange almost any trip.
Real Estate. Real estate transactions are an ideal area for e-commerce. The customer can view many properties, sort and organize properties according to preferences and can preview the exterior and interior designs of the properties, shortening the search process.
Delivery of services (buying an airline ticket or stocks) can be done 100 percent electronically, with considerable cost reduction potential. Therefore, online services is growing very rapidly.

92
E-Commerce Support Services
These services include: e-infrastructure (mostly technology consultants,
system developers and integrators, hosting, security, and networks)
e-process (mainly payments and logistics)
e-markets (mostly marketing and advertising)
e-communities (different audiences and business partners)
e-services (CRM, PRM, and directory services)
e-content (supplied by content providers)
B2B and B2C applications require payments and order fulfillment. Portals require content, etc.

93
E-Commerce Support Services
Electronic checks (e-checks) are similar to regular checks. They are used mostly in B2B
Electronic credit cards make it possible to charge online payments to one's credit card account.
Purchasing cards, the B2B equivalent of electronic credit cards. Electronic cash (e-cash) appears in three major forms: stored-
value cards, smart cards, and person-to-person payments. Electronic Bill Presentment and Payments allow customers to
pay their recurring monthly bills, such as telephone, utilities, credit cards, etc. online.
E-wallets are mechanisms that provide security measures to EC purchasing. The wallet stores the financial information of the buyer, including credit card number, shipping information, and more.
Virtual credit cards are a service that allow you to shop with an ID number and a password instead of with a credit card number.
Electronic Payments are an integral part of doing business, whether in the traditional way or online. Unfortunately, in most cases traditional payment systems are not effective for EC, especially for B2B.

94
E-Commerce Support Services

95
E-Government
It can be divided into three major categories:
government-to-citizens (G2C) government-to-business (G2B) government-to-government (G2G)
E-government is the use of Internet technology in general and e-commerce in particular to deliver information and public services to citizens, business partners and suppliers, and those working in the public sector.

96
Consumer-To-Consumer – C2C
C2C Auctions. Classified Ads. Personal Services. Support Services to C2C.
Customer-to-customer (C2C) e-commerce refers to e-commerce in which both the buyer and the seller are individuals (not businesses). C2C is conducted in several ways on the Internet, where the best-known C2C activities are auctions.