Windows mobile architecture_overview
-
Upload
danieldowns1 -
Category
Technology
-
view
470 -
download
2
description
Transcript of Windows mobile architecture_overview

Architectural Overview of Windows Mobile Infrastructure Components Windows Mobile 5.0 and 6-powered Devices
White Paper
Published: May 2007
For the latest information, please see http://www.microsoft.com/windows/mobile/
Abstract
This whitepaper describes how mobile devices running Windows Mobile 5.0 and Windows Mobile 6 are fully integrated into Microsoft’s server infrastructure, and how the components fit together. The paper goes over the fundamental design requirements for employing Microsoft infrastructure components to help secure and manage mobile devices. The following components and their interrelationships are discussed: Exchange Server 2003 and 2007, Exchange ActiveSync, Internet Security and Acceleration Server 2004 and 2006, Microsoft Dynamics Platform, Small Business Server 2003, Microsoft Operations Manager (MOM) 2005 and Systems Center Operations Manager (SCOM) 2007, Systems Management Server (SMS) 2003 and Systems Center Configuration Manager 2007, Microsoft Office SharePoint Server 2007 and Live Communications Server 2005.

The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication.
This white paper is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS DOCUMENT.
Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in, or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), or for any purpose, without the express written permission of Microsoft Corporation.
Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property.
© 2006 Microsoft Corporation. All rights reserved.
The example companies, organizations, products, domain names, e-mail addresses, logos, people, places, and events depicted herein are fictitious. No association with any real company, organization, product, domain name, e-mail address, logo, person, place, or event is intended or should be inferred.
Microsoft, Active Sync, Outlook, Windows, Windows Mobile, Windows Server, and the Windows logo are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries.
The names of actual companies and products mentioned herein may be the trademarks of their respective owners.

Overview
In an enterprise environment, properly leveraging mobility involves much more than buying Windows
Mobile enabled devices. In this whitepaper, you will learn how mobile devices running Windows Mobile
5.0 and Windows Mobile 6 are fully integrated into Microsoft’s server infrastructure, and how the
components fit together to provide immediate value to your enterprise. After reading this overview,
you should be familiar with the fundamental design requirements for employing Microsoft
infrastructure components to help secure and manage your mobile devices.
The Microsoft mobility platform is comprised of several key components. Because email and messaging
is such an important application of information technology, Exchange Server is a key component of the
architecture. Additionally, your firewall solution serves to enhance security. Other components, such as
Systems Management Server 2003 and Systems Center Operations Manager 2007 (formerly Microsoft
Operations Manager) are available to manage and control the operations of the infrastructure. You will
also learn how the Windows Mobile platform allows you to reuse much of your Line of Business
application investment and personnel skill sets. The infrastructure components and the development
platforms form work together to drive one seamless, cost effective and scalable solution with enhanced
security for your enterprise.
Mobility Architecture Goals
Microsoft’s mobility architecture is designed to integrate with your existing environment, and allow you
to reuse existing systems administration skill sets. The following are some of the design goals of the
architecture:
Flexibility. In most enterprises, IT infrastructure is heterogeneous. Microsoft mobility architecture is designed to work with your existing environment, such as a variety of advanced firewall solutions, network topologies, and 3rd party device management products. While this whitepaper addresses Microsoft components and recommended architecture, the architecture is modular and was designed to work with other designs and products. This allows you to leverage your investment in such areas such as security, scalability, and manageability. This works for both enterprise messaging applications and line of business applications – no new special setup is necessary for security and authentication.
Scalability. Most enterprises already have a scalable infrastructure for managing their server and desktop environments. Mobility should be viewed as just another piece of overall management strategy. Therefore, Windows mobility architecture relies on existing infrastructure, such as Exchange 2007 or 2003, for scalability and high availability. No new middle tier servers, which can result in a single point of failure, are required for the architecture.
Manageability. Microsoft architecture supports many points of management, such as Exchange console, Systems Management Server 2003 or the upcoming Systems Center Configuration Manager 2007, or operations monitoring through Systems Center Operations Manager 2007 or Microsoft Operations Manager 2005. This allows different levels of management, depending on

existing infrastructure investment. Third-party device management products are supported as well.
Extensibility. The architecture is the basis on top of which other Microsoft and third party applications are built. It has built-in support for Microsoft Office SharePoint Server, and Live Communications Server 2005. A multitude of third party applications works with the infrastructure. Additionally, Microsoft Dynamics ERP and CRM applications use the same infrastructure to deliver their functionality.
Security. Windows Mobile Operating Systems are designed with security in mind and form an integral part of the infrastructure. Windows Mobile cryptography services have been certified with US Federal Information Processing Standard (FIPS) 140-2, level 1. Additionally, there is support for dual-factor authentication, 256-bit AES encryption, remote device wipe and application certificates. Additionally, the Internet Security and Acceleration 2006 Server has features that integrate with components on the corporate networks, such as analysis of Exchange traffic that flows to and from mobile devices.
Reuse of Existing Skill Sets. Both on the administration and application development sides, same familiar tools are used. For systems management, mobile devices are treated as just another type of asset from management tools perspective. For application development, development for both Mobile Web using ASP.NET 2.0 and Mobile Smart Client using the Compact Framework offer a similar development environment and APIs.
Overview of Windows Mobile Security
Windows Mobile operating systems play a key role in enterprise mobility infrastructure through their
support of communication security standards, security policies and features designed for remote policy-
based management. Windows Mobile 5.0 with Messaging and Security Feature Pack (MSFP) and the
new Windows Mobile 6 both have a sophisticated security system to protect the device from running
malicious code and to help secure communications with corporate servers. As an enterprise
administrator, you are responsible for provisioning and managing security policies on devices and thus
need to understand Windows Mobile features that support communications and device security.
Windows Mobile Application and Network Security
Mobile devices face many threats in today’s environment. To address these threats, digital certificates
are used both to ensure both application and communication security. In the first role, certificates help
Windows Mobile to determine whether an application can be run on the device, and what level of
privilege it receives. Furthermore, most applications are restricted from writing to the registry and
other services that might compromise security. This prevents malicious code from infecting the device
and gives administrators tight control over the applications that are installed on the device. Some
manufacturers even put additional restrictions that require all applications to be signed by a known
trusted authority in order to run.
In securing communications, Windows Mobile uses digital certificates to establish a network connection
using Secure Sockets Layer (SSL) and validate the identity of the server using its installed root
certificates. Windows Mobile offers cryptographic services for:

Data encryption - to help secure communications
Hashing - to help ensure data integrity
Digital signatures – to verify identity
SSL is used to enhance security of communications for applications such as Mobile Outlook client
connecting to an Exchange Server, Line of Business applications connecting over web services, or
database clients connecting to a central data store.
The cryptography services have been certified with the US Federal Information Processing Standard
(FIPS) 140-2, level 1. The certification designates that Windows Mobile security algorithms work
properly and protect against a variety of threats. Additionally, Windows Mobile supports Virtual Private
Networking (VPN), Wi-Fi encryption, Storage Card Encryption, and two-factor authentication systems
like RSA SecureID. Lastly, Windows Mobile supports Certificate-Based Authentication, in which each
device is issued a digital certificate that uniquely identifies the device and encrypts the connection.
For more information on security model in Windows Mobile please see Security Model for Windows
Mobile 5.0 and Windows Mobile 6, Windows Mobile 5.0 Application Security.
Windows Mobile Security Policies Security policies are used for device management; they define levels of security. The policies dictate
whether a device can be configured over the air (OTA), and whether to accept unsigned messages,
applications, or files. The policies include settings such as the number of login attempts before local
device wipe, password strength and length, and PIN-based device protection. Additionally, Windows
Mobile 5.0 and 6 include ability to remotely wipe the device, or locally wipe it after administrator-
settable number of incorrect password entry attempts. By default, only a manager of the device can
change security policies. The policies can be configured through a central management system such as
SMS 2003 or mobile management features built into Exchange 2003 and 2007, provided the OEM or
Mobile Operator has given the administrator Manager permissions. For more information on
management capabilities of SMS 2003 and Exchange, please see references in related sections of this
whitepaper.
Exchange Deployment and Mobile Device
Management
Today, every computer user is also an email user, so Exchange Server is central in enterprise
deployments. Mobile devices communicate with Exchange for a variety of services including email, data
synchronization and security. Understanding Exchange deployment topologies will give you the
background you need to leverage Microsoft Exchange with your mobile devices. Additionally, Exchange
has features that support over-the-air management, data synchronization, and security of mobile
devices through Exchange ActiveSync. Exchange ActiveSync works directly with the Windows Mobile 5.0
and 6 operating systems so you can avoid the added cost of middleware or service fees.

Exchange 2003 Deployment Topologies
Exchange 2003 is a highly scalable enterprise messaging environment designed to support many types of
clients. For large enterprises deploying several thousand devices and tens, or even hundreds of
thousands users, Exchange 2003 allows to distribute load across multiple servers. Exchange 2003
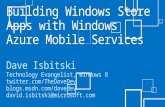
allows deployment using two types of servers – front-end and back-end. This topology is shown in
Figure 1.
Front-end servers accept all of the communications with the clients outside the corporate network.
They use a proxy mechanism to transfer requests to the correct back-end servers on behalf of client
computers and devices. They can be configured to support Outlook Web Access (OWA), Outlook
Mobile Access (OMA), Exchange ActiveSync for mobile devices, and RPC over HTTPs. Front-end servers
use Active Directory to find the correct back-end server, where the user’s mailboxes are stored. The
front-end – back-end topology results in a highly scalable solution, as the front-end servers take the load
off the back-end servers. The front-end and back-end topology should be used by large organizations; it
results in decreased management costs, and provides better performance and fault tolerance.
Additional elements in the figure, such as SCCM 2007 Device Management and SCOM 2007 Operations
Monitoring, are discussed later in the whitepaper.
Advanced
Firewall
Exchange,
AD and Firewall Monitoring
AD Monitoring
AD Server
Back-End Server 1
Front-End
Server
Back-End Server 2
Look up
User’s Mailbox
Location
SCCM 2007 –
Common Management
Infrastructure for
Desktop / Server /
Mobile Environments
Perimeter
Network
SCOM 2007
or MOM 2005
Common
Monitoring Infrastructure
Device Management
Point
Exchange Farm
SSL Bridging
Internet
HTTPS
Device Distribution Point Primary Site Server
Site Database
Exchange
Monitoring
Corporate
NetworkSM
S M
onito
ring
Figure 1 Mobile Infrastructure Architecture Including Exchange 2003 Front-end and Back-End Topology
The mobile device communicates with the front-end server. All email, task, calendar, and other data
synchronization operations are coordinated through the front-end server. Because the front-end

servers are responsible for client communication, this topology has several advantages in mobile
scenarios:
1) A single server name is exposed to the users for accessing Exchange. Addition of new servers is
transparent to the user.
2) SSL Encryption and Decryption can happen on the front-end server, thus offloading this operation
from the back-end servers and saving resources.
3) To enhance security of front-end servers, they can be put into a perimeter network creating an
additional layer of protection between the front-end and back-end servers.
Many organizations with a smaller number of users choose to run Exchange on a single server. This also
works well for testing purposes. However, to achieve scalability and security advantages, Microsoft
recommends the front-end, back-end architecture.
For more information please see the following resources:
Exchange Server 2003 and Exchange 2000 Server Front-End and Back-End Topologies
Step-by-Step Guide to Deploying Windows Mobile-based Devices with Microsoft Exchange
Server 2003 SP2
Microsoft Exchange Server 2003 Client Access Guide.
Exchange 2007 Server Roles
Exchange 2007 introduces the concept of server roles as the primary mechanism of scalability. Each
server can act as one or more roles within the topology. Mobile users are supported by a special server
role called the Client Access Server, which is analogous to the front-end server in Exchange 2003. Client
Access Server has interfaces for Exchange ActiveSync, Outlook Web Access, and RPC over HTTPS. The
Mailbox and Hub Transport server roles in combination are similar to the back-end server in Exchange
2003. The Mailbox Server role is the storage server that hosts mailboxes and public folders while the
Hub Transport Server role is responsible for routing mail.
For more information please see The Fundamentals of Mobile Access to Exchange 2007.
Exchange ActiveSync
Exchange ActiveSync is a part of Exchange Server 2003 and 2007 that is optimized to deal with high-
latency / low-bandwidth networks, and also with clients that have limited amounts of memory and
storage. Exchange ActiveSync supports Direct Push technology which automatically synchronizes (or
“pushes”) new email to mobile devices as soon as the mail arrives. Direct Push is in contrast to a polling
style where the device has to request new email from the server on a timed basis. Under the covers,
the Exchange ActiveSync protocol is based on HTTP, SSL, and WBXML, so the communications channel
has enhanced security. Exchange ActiveSync is enabled out of the box on all user mailboxes without
any additional software or servers.
Mobile devices interact with Exchange ActiveSync on the front-end servers when synchronizing email,
schedules, contact information and tasks to the device. Synchronization is extremely fast, with

enhanced data compression that enables rapid sending and receiving of messages. Because Exchange
ActiveSync uses standard transport protocols, there is no need to buy special data plans from mobile
operators; standard data plans can be used for global mobile access. It supports all types of mobile
communication networks, including GSM, GPRS, UMTS, HSDPA, and CDMA.
Microsoft Exchange Server 2007 adds several productivity-enhancing features to Exchange ActiveSync.
It includes support for flags, HTML mail, and allows users to search the entirety of their mailboxes from
the mobile device, including messages not currently synced to the device. This helps overcome the
limited resources of a mobile device, and not limiting access to just the portion that fits in device
memory.
For more information, including Exchange ActiveSync features for Exchange 2003 and Exchange 2007,
please see Mobile Messaging with Exchange ActiveSync
Mobile Device Management through Exchange ActiveSync Since Exchange is so central in many enterprise deployments, Microsoft added special administrative
features into Exchange which can allow mobile devices to adhere to the organization's security policies.
This native device management support helps reduce complexity and costs because you can reuse
existing infrastructure.
Security policies are set on the Exchange 2003 server and delivered to the client through Exchange
ActiveSync. When a mobile device security policy is defined on the server, it is automatically sent to
each device the next time the user of the device starts synchronization. The Exchange 2003 ActiveSync
Mobile Administration Web tool enables administrators to manage the process of remotely erasing lost,
stolen, or otherwise compromised mobile devices.
With Exchange Server 2007, mobile device management is integrated into the Exchange Server
Management Console and self-service capabilities are exposed via Outlook Web Access. For example,
when the device is lost or stolen, users can wipe data from their device themselves, rather than calling
the corporate helpdesk. By doing this, Exchange Server 2007 helps to drive down the cost of supporting
mobile messaging. With Exchange Server 2007, the system administrators can define and name
multiple sets of security policies and apply them to individual users or to different user groups in Active
Directory. They also have access to enhanced monitoring and logging for operational monitoring.
For information on Exchange ActiveSync in Exchange 2007, see Overview of Exchange ActiveSync .
Exchange ActiveSync Communication Security
To help secure Exchange ActiveSync traffic, encryption through Secure Sockets Layer (SSL) is necessary.
If your organization currently exposes Outlook Web Access (OWA), you already have the infrastructure
in place to support a mobile deployment using high-grade, 128-bit SSL encryption. Because Exchange
ActiveSync is implemented as an application that runs on Internet Information Services (IIS), its security
settings can be configured using the same certificates you’re already using for OWA. All communication
between the Windows Mobile device and the Exchange front-end server take place over a single TCP/IP

port: TCP port 443, used for SSL-secured HTTP traffic. This greatly simplifies enterprise firewall
configuration, because only a single port needs to be opened from the Internet to the Exchange
ActiveSync front-end server, and that port will probably be open in any case because it’s the same port
used for Outlook Web Access. Additionally, more advanced security scenarios are supported by
Exchange Server and Windows Mobile, such as S/MIME messaging, and SecureID or certificate-based
authentication.
For more information on securing communications with SSL, please see the Step-by-Step Guide to
Deploying Windows Mobile-based Devices with Microsoft Exchange Server 2003 SP2 and Mobile Secure
Certificates Whitepaper.
Communication Security and Advanced Firewall Configurations
Most enterprises use a combination of hardware and software firewall solutions, such as Internet
Security and Acceleration (ISA) Server 2004 or 2006. In addition to the ISA Servers, Exchange supports
most other reverse proxy software firewall products available on the market. Typically, the advanced
firewall is deployed in the perimeter network (see Figure 1). Existing IIS website already used for RPC
over HTTPS or Outlook Web Access is used, so usually no new inbound ports need to be opened on the
firewall. Exchange ActiveSync communicates through a different virtual directory, and the ISA server
can be configured to examine Exchange ActiveSync traffic. SSL is applied between the client and ISA
server, and between the ISA server and the front-end server. This is called terminate – initiate, or SSL
bridging.
SSL bridging protects against attacks that are hidden in SSL-encrypted connections. ISA is configured to
decrypt and examine Exchange traffic from the client, terminating the SSL connection. This step
prevents any malicious traffic from getting into the corporate network, protecting it from any threats.
ISA Web publishing rules configure the connection to the Exchange front-end server. If the rule specifies
to forward the request using HTTPS, ISA 2006 then initiates a new SSL session to the Front-End
(Exchange 2003) or Client Access (Exchange 2007) Server. The second SSL session ensures that the
communication is safe from a malicious user already inside the firewall.
For more information about ISA and Exchange deployment scenarios please see one of the following
documents:
Security for Windows Mobile Messaging in the Enterprise
Publishing Exchange Server 2007 with ISA Server 2006
Using ISA Server 2004 with Exchange Server 2003
Publishing Exchange Server 2003 with ISA Server 2006
Exchange Scalability Mobile devices represent a relatively light load on the Exchange servers compared to Outlook Web
Access or RPC/HTTP, so your infrastructure may be able to support the extra load without adding
additional servers. When rolling out Exchange ActiveSync at Microsoft to 26,000 users, Microsoft IT

found that only 3.6% of the load on their servers being due to Exchange ActiveSync, and thus did not
need to add any new servers.
The front-end and back-end architecture provides several client access performance and availability
benefits. The front-end servers offload some load processing duties from the back-end servers.
Therefore, front-end servers do not need large or particularly fast disk storage, but should have fast
CPUs and a large amount of memory. Microsoft provides several tools, such as the Exchange Server
Load Simulator tool (LoadSim) and the Exchange Server Stress and Performance (ESP) 2003 tool to test
the performance of Exchange Servers. These tools allow better planning of performance and scalability
requirements of Exchange infrastructure.
Through continuous monitoring with operations tools such as MOM 2005 or SCOM 2007 (see below),
administrators can monitor trends and pinpoint performance degradation. They can then provision
additional back-end servers to decrease the load on existing infrastructure and move mailboxes over to
the new servers. Since the clients use one URL for all their communications with the front-end servers,
back-end servers can be added transparently to the users. For Exchange 2007, the scalability efforts are
focused on the Mailbox and the Hub Transport server roles. Exchange Server architecture should
always include some planned redundancy in order to effectively handle peak loads and unforeseen
events.
Office SharePoint Server 2007 and Live Communications Server (LCS) 2005
Microsoft Office SharePoint Server (MOSS) 2007 web portal technology supports mobile devices out-of-
the-box. Every list and library in MOSS 2007 or Windows SharePoint Services (WSS) v3 is capable of
hosting ‘Mobile Views’. These are standard views of lists or libraries that an administrator has defined as
being mobile enabled. Individual list items can be viewed in mobile form and InfoPath forms can be
opened in a mobile client via a web browser interface. Additionally, Exchange 2007 and Windows
Mobile 6 enable access to files stored on WSS sites and Universal Naming Convention (UNC) file shares via
embedded Exchange links.
Microsoft Office Communicator Mobile allows users to use Microsoft Live Communications Server (LCS)
2005 SP1 on the mobile device. This allows the mobile users to use instant messaging to communicate
with their co-workers who are on the corporate network, all the while taking advantage of enterprise
features such as more secure communications and centralized logging and auditing. Communicator
Mobile provides integration between multiple mobile applications such as Voice over IP (VoIP), presence
status information and organization’s address book. Additionally, users can also communicate with
partners or public instant messaging service users.
For more information please see Microsoft Office Communicator Mobile Planning and Deployment
Guide.
Mobile Device Management and Operations

In addition to Exchange-based device management, Systems Management Server (SMS) 2003 Device
Management Pack provides features for device management using an interface already familiar to
administrators. Microsoft Operations Manager (MOM) 2005 allows operational monitoring of
enterprise infrastructure, and the Exchange Management Pack for MOM 2005 has features to monitor
mobile device performance.
Mobile Device Management
Systems Management Server (SMS) 2003 Device Management Feature Pack enables management of
mobile devices when they are connected on the corporate network, or through the VPN. It allows SMS
to collect hardware and software inventory information, distribute and install software, execute scripts
and manage security policies and other settings on devices. SMS is fully integrated with Active
Directory and allows management at levels of different granularity. This is done in one central place
through an Administrative GUI. Importantly, SMS Device Management Feature Pack allows reusing the
same common infrastructure that is already being used for Server, Laptop, and Desktop management.
Systems Management Server works by installing an agent on the mobile device, and using the agent to
collect information about the device, as well as perform management functions. The agent gets
installed during a desktop ActiveSync session and after that enables management of the devices when
on the corporate network. SMS 2003 supports multiple device management and device distribution
points, thus providing a scalable solution. Please see the SMS 2003 Device Management Feature Pack
Site for more information.
The System Center Configuration Manager (SCCM) 2007, scheduled for release in second half of 2007,
is a new version of SMS that builds on the features included with SMS 2003. It adds support for smart
phones and over-the-air software distribution from gateway located in a corporate DMZ (see Figure 1).
The user no longer has to be on the corporate network to get software updates. The device must enroll
for a client certificate during the setup process to be manageable from the internet.
For more information please see the System Center Configuration Manager 2007 site.
Operations Management
Microsoft Operations Manager (MOM) 2005 with Exchange Management Pack monitors the Exchange
Servers including some aspects of the mobile device operations. MOM uses event log entries and
special performance counters on Exchange Servers to collect information. It allows administrators to
monitor all aspects of the Exchange Server, including protocol metrics, events generated by Exchange,
server performance, and mobility features.
MOM 2005 monitors the heartbeat interval and synchronization latency of mobile devices, giving the
administrators a good indication of the mobile user’s experience. System administrators can then make
decisions about how to tune or to scale Exchange components once they notice performance
degradation.

The new version of MOM, the Systems Center Operations Manager (SCOM) 2007 together with the
SCOM Exchange Management Pack extend the advances of the MOM platform and provide more
advanced rule-based availability and performance monitoring. MOM 2005 and SCOM 2007 both
support a consolidated view of the entire enterprise infrastructure tiered deployment architecture that
can scale up to hundreds of thousands of clients.
For more information on MOM 2005 please see the Exchange Server Management Pack Guide for MOM
2005. For more information on SCOM 2007 please see the Systems Center Operations Manager 2007
Site.
Application Design and Development
Windows Mobile 5.0 and 6 are supported by one of the largest catalogs of Line of Business (LOB)
applications, offered both by Microsoft and third-party ISVs. However, to meet specific needs of many
enterprises, customers need to develop their own mobile applications. The infrastructure elements
described above combine into a platform for deploying and managing Line of Business applications.
Mobile applications use the same common infrastructure already being used for desktop and server
applications, leading to reduced complexity and lower deployment costs. Common design and
architecture issues, such as development, deployment, operations, and communication security have
well defined solutions. Development frameworks, databases and tools that are common to both
traditional and mobile development allow organizations to reuse much of their existing application
investment and the skill set of their personnel.
Windows Mobile 5.0 and 6 support the .NET Compact Framework, a specialized mobile platform for
developing applications that is based on Microsoft’s .NET. Compact Framework allows application
developers to use the same development languages and tools they are using to develop Windows and
Web-based applications. Both C# and VB.NET languages are supported, and Compact Framework has
built-in support in state-of-the-art Visual Studio 2005 Integrated Development Environment. Available
emulator tools simplify application development and testing on different types of devices.
Additionally, Microsoft provides many resources and tools for mobile development, including recently
released the Mobile Client Software Factory, which provides a framework and application blocks for
commonly used smart client application scenarios. For example, it includes a library that allows queuing
of web service calls to the server when the device is disconnected, and optimizes data transmission
depending on the network speed. For more information on Compact Framework, please see .NET
Compact Framework site.
Mobile database-based applications can take advantage of SQL Server 2005 Compact Edition. SQL
Server 2005 Compact Edition deployed on a device works with a central SQL Server 2005 database
server to synchronize data with the device. SQL Server 2005 supports ability to target each user and
device with a small subset of the enterprise database to reduce the storage requirements on the device.
Advanced mobile database scenarios such as merge replication allow database engine to synchronize
the local database that resides on the mobile device with a central database running on a server.

Developers access the database using Visual Studio 2005 development system and the familiar ADO.NET
mechanism supported by all SQL Server editions. In addition to mobile devices, the Compact Edition is
supported on other Windows platforms, including tablet PCs, and desktops. In many single-user client
applications, this means that the same code can be reused on all Windows platforms. For more
information on mobile database development, please see the SQL Server 2005 Compact Edition site.
Many Line of Business (LOB) applications are web-based or web-services based. Internet Information
Server (IIS) and ISA 2004 and 2006 allow advanced security configurations of applications, including
authentication and security rules targeted to specific applications. The network connections are
typically encrypted using SSL and the clients must authenticate themselves against the corporate
firewall server and Active Directory. For the environments using Service Oriented Architecture, mobile
devices often become just another client accessing the SOA web services.
Microsoft LOB applications also support Windows Mobile computing platforms. Microsoft Dynamics
software, such as Microsoft Dynamics AX, and Microsoft Dynamics CRM have out-of-the-box support for
mobile access. Dynamics AX offers a mini mobile ERP client called the Mobile Sales Assistance. It allows
the sales force to examine their route plans, email and calendar, point of sale information for each
costumer, and product and inventory data. There is also Mobile Business Assistant to assist business
decision makers in understanding business performance and tracking KPI metrics of a business.
Dynamics CRM 3.0 was also designed with the mobile sales force in mind. CRM Mobile Express, a
Microsoft Dynamics CRM 3.0 mobility application, enables users to instantly view, create, and modify
data on any Internet-capable device. It lets a salesperson in the field tap into the same sales, marketing,
and customer service data they have access to in the office. CRM Mobile Express runs in a Web browser
and doesn't require users to install additional software.
Mobile Device Support in Small Business
Server 2003
For smaller businesses that require only mail and file share, Microsoft recommends SBS server. Small
Business Server (SBS) 2003 R2 is an “all-in-one” server solution designed for small businesses. It is a
single server that is designed to perform the functions of the IT infrastructure in larger environments, at
a much lower cost. It provides the following services: Exchange 2003, Active Directory, DHCP, DNS,
Domain Controller, Monitoring and Management Services and Windows SharePoint Services. SBS 2003
R2 Premium version also includes SQL Server 2005 Workgroup, ISA Server 2004 and Microsoft FrontPage
2003.
SBS 2003 R2 supports mobile devices through Exchange mobility features offered in Exchange SP2
including Exchange ActiveSync access, this can be configured using SBS’s group policy (similar
functionality to SMS 2003). A key limitation of the SBS server is that only 75 users, computers, or
devices can connect to the server at one time, so adding mobile devices will count against the total limit
that the SBS server will support.

For more information and how-to instructions please see Deploying Windows Mobile 5.0 with Windows
Small Business Server 2003.
Conclusion
Properly supporting mobile devices in an enterprise environment requires interaction of several
different areas of enterprise architecture, software security, and operational support tools. Once you
understand the broad components of communications (Exchange ActiveSync), security (SSL and
certificates), management and operations (Exchange ActiveSync, Microsoft Operations Manager,
Systems Management Server), and how they fit together with LOB applications and back-end servers,
you can work with your enterprise security, administration, infrastructure and management teams to
make the most out of your mobile device investment. Since these are familiar tools that are likely
already being used to manage your Windows desktop and server infrastructure, you can expand the use
of existing infrastructure components without additional training or server costs. The Windows Mobile
Operating System and the Windows Server platform elements all work together to drive a security-
enhanced, seamless, cost effective, and scalable solution that addresses all major issues in mobile
enterprise environment.
Additional Resources:
Mobile Messaging at Microsoft: Improving Security, Manageability, and User Experience
Mobile Strategy White Papers Site
Exchange 2007 Support for mobile Devices