Top 10 Things to Secure on iOS and Android to Protect Corporate Information
-
Upload
lumension -
Category
Technology
-
view
187 -
download
2
description
Transcript of Top 10 Things to Secure on iOS and Android to Protect Corporate Information

Sponsored byTop 8 Things to Secure on iOS and Android to
Protect Corporate Information
© 2013 Monterey Technology Group Inc.

Thanks to
© 2013 Monterey Technology Group Inc.
www.Lumension.com

Preview of Key Points
1. Unattended control
2. Password complexity
3. Encryption
4. Remote lock
5. Remote wipe
6. Jailbroken/rooted detection
7. Hardware/software inventory
8. Device feature restrictions
9. The Carrot

Reality Check
Biggest risk Lost and stolen devices
Legal issue BYOD with MDM

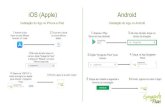
1Unattended control(aka PIN/Password)
iOS
Options PIN Password Touch ID
When to kick in Single threshold
Brute force defense Optional erase after
10 entries Increasing delay
Android
Options PIN Password Pattern Face
When to kick in More sophisticated
Brute force defense Optional erase after X
entries Increasing delay
Auto account wipe

2Password complexity
iOS
Allow simple value
Require alphanumeric value
Minimum passcode length
Minimum number of complex characters
Maximum passcode age
Passcode history
Auto-lock timeout
Grace period for device lock
Maximum number of failed attempts
Allow Touch ID
Android
Password enabled
Minimum password length
Alphanumeric password required
Complex password required
Minimum letters required in password
Minimum lowercase letters required in password
Minimum non-letter characters required in password
Minimum numerical digits required in password
Minimum symbols required in password
Minimum uppercase letters required in password
Password expiration timeout
Password history restriction
Maximum failed password attempts
Maximum inactivity time lock

3Encryption
iOS This is complicated
2 levels or encryption
First level encrypts all storage
But only for purpose of quickly wiping – doesn’t protect data
2nd level encrypts data of supporting applications
Such as email
Unclear whether jailbreaking can defeat encryption
Android
Based on tried and tested Linux dm-crypt
Encryption ultimately based on passcode
Only encrypts /data partition
Some devices offer SD card encryption
This is not your PC’s BitLocker

4Remote lock
iOS
Protect lost phones in hopes of recovering
Unlikely to defend against jailbreaking
Android
Same purpose
Unclear how secure

5Remote wipe
iOS
Wipes encryption key used to encrypted entire device
Fast and effective
To defeat, must jailbreak before wipe instruction received
Android
Does a fast erase and not a secure erase of the SD card

6Jailbroken/rooted detection
iOS
Important to detect because jailbroken devices can run software from any source
Android
Rooted
Unlocked boot loader
Custom recovery
USB debugging enabled (allows ADB)

7Hardware/software inventory
Health
iOS
Important because different devices have different vulnerabilities and jailbreak options
Android
Important because different devices have different vulnerabilities and security compliance
Android security features vary by version
But more importantly by brand because of fragmentation
Encryption fails on multi-user devices

8Device feature restrictions
iOS
App installs, camera use, screen capture, iTunes store usage, in app purchases
Force encrypted backups
JavaScript
Allow Touch ID
Supervised restrictions Other store usage,
allow app removal
Android
Require storage encryption
Disable camera

9The Carrot
iOS
WiFi configuration
Exchange configuration
Android
WiFi configuration
Exchange configuration

Bottom line
Key requirements Stay up on device health and inventory Enforce password and encryption Discourage older devices Remote wipe
Hone procedure Use carrots
Mobile Device Management Another security solution to manage? Mobile devices are just another type of endpoint Manage iOS and Android devices along with Windows
endpoints on the same pane of glass

L.E.M.S.S. Mobile Device Management
17 June 2014
Dee LiebensteinVice President Product Management

Unifies workflows and technologies to deliver enhanced capabilities in the management of endpoint operations, security and compliance
Lumension Platform Benefits
16
Endpoint Operations Endpoint Security
Device ControlDevice Control
Asset Management
Asset Management
Software Management
Software Management
Power Management
Power Management
Configuration ManagementConfiguration Management
Mobile Device ManagementMobile Device Management
ReportingReporting
Data EncryptionData Encryption
Antivirus/SpywareAntivirus/Spyware
Patch Management
Patch Management Application
ControlApplication
Control
FirewallManagement
FirewallManagement
Mobile DevicesMobile Devices
DesktopsDesktops
LaptopsLaptops
ServersServers

Lumension MDM Capabilities Overview
17
L.E.M.S.S. Integration Device Management Device & Data Security
Integrated Management iOS / Android Enrollment via App
Remote Lock
Localized Console & Apps AD Authentication Remote Wipe
Per-device Licensing Device Administration (Delete/Disable/Offline)
Password Enablement (Enforcement / Clearing)
Role-based Access Control (RBAC)
Check-in Interval: Configurable and On-Demand
Password Complexity Configuration
Manage Mobile Endpoints Hardware Inventory Device Encryption Enforcement
iOS and Android Support Managed Devices Dashboard / Reporting
Device Feature Restrictions
Consistent Policy Workflow Root/Jailbreak Detection (Device Health)
Exchange Configuration (iOS)
Over the Air Management Action Traceability Wi-Fi Configuration

Free Device Scanner tool – discover all the devices being used in your network~/Resources/Security-Tools
More on BYOD issues and solutions in the Lumension Optimal Security blog atblog.lumension.com/tag/byod
More Information at www.lumension.com
18
More information on the Lumension MDM at~/mobile-device-management-software
Get the 2013 BYOD Survey Report at~/more-info/BYOD-and-Mobile-Security