Unsupervised learning Networks Associative Memory Networks ELE571 Digital Neural Networks.
Networks
-
Upload
hi-tech-criminal-justice -
Category
Education
-
view
893 -
download
4
description
Transcript of Networks

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
Police Technology Police Technology Chapter FourChapter Four
NetworksNetworks

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
Learning ObjectivesLearning Objectives Understand the importance and use Understand the importance and use
of of NetworksNetworks Understand the different types of Understand the different types of
technologies necessary to establish a technologies necessary to establish a networknetwork
Be exposed to several different types Be exposed to several different types of networksof networks
Understand the necessity for network Understand the necessity for network security and several of the means of security and several of the means of providing network security.providing network security.

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
Network BasicsNetwork Basics
A A networknetwork is about is about two or more people two or more people establishing a way to establishing a way to communicate.communicate.
There are formal and There are formal and informal networks. informal networks.

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
Network BasicsNetwork Basics
Networks are founded on the concept Networks are founded on the concept of of client-server architectureclient-server architecture. . Architecture refers to the design of a Architecture refers to the design of a system or technology. system or technology.
The individual work station, called a The individual work station, called a nodenode, is provided networking , is provided networking services by a server. services by a server.

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
Network BasicsNetwork Basics
The The serverserver is a computer is a computer that provides files, that provides files, printers, and processing printers, and processing power to the individual power to the individual workstations. The server is workstations. The server is a special type of computer a special type of computer linked into a network. It is linked into a network. It is used only to manage the used only to manage the network, shared data, and network, shared data, and shared resources. shared resources.

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
Why Network?Why Network? Law enforcement agencies may have Law enforcement agencies may have
many buildings and offices in different many buildings and offices in different physical locations. A network allows physical locations. A network allows them to share computer, data, and them to share computer, data, and information resources. Much of the information resources. Much of the information used by law enforcement information used by law enforcement comes from agencies outside their comes from agencies outside their organization (e.g., DMV, Corrections, organization (e.g., DMV, Corrections, other agencies, etc.). other agencies, etc.).

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
Networks also provide organizations Networks also provide organizations with the capability to back up data. with the capability to back up data. If one computer fails, the network If one computer fails, the network can take over the processing load. can take over the processing load.
Why Network?Why Network?

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
Back to …..Back to …..Analog and Digital SignalsAnalog and Digital Signals
An analog signal weakens as it travels An analog signal weakens as it travels through wire because of the resistance through wire because of the resistance the signal meets in the the signal meets in the mediummedium that is that is carrying it (air, wire, coaxial cable). carrying it (air, wire, coaxial cable).
Digital signals are subject to the same Digital signals are subject to the same decrease in strength as analog signals. decrease in strength as analog signals.

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
Digital signals are the primary means ofDigital signals are the primary means of
transmitting data communications.transmitting data communications.
Digital signals have several advantagesDigital signals have several advantages
over analog: over analog: Fewer errors; Fewer errors; Can be transmitted at higher speedsCan be transmitted at higher speeds Peripheral devices are less complexPeripheral devices are less complex..
Back to …..Back to …..Analog and Digital SignalsAnalog and Digital Signals

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
The analog wave is called a The analog wave is called a baudbaud. Bits are essentially . Bits are essentially added to the analog wave. added to the analog wave.
Public networks tend to run at Public networks tend to run at about 2,400 baud (waves) per about 2,400 baud (waves) per second. second.
Analog stuffAnalog stuff

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
Our technology adds more bits to Our technology adds more bits to each baud generally in multiples each baud generally in multiples of four.of four.
A 2,400 baud analog signal that A 2,400 baud analog signal that adds 12 bits to each baud would adds 12 bits to each baud would give an effective transmission give an effective transmission rate of 28,800 bits per second rate of 28,800 bits per second (BPS).(BPS).
Analog stuffAnalog stuff
This about Modem Speed!

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
One of the schemes commonly used toOne of the schemes commonly used toprevent data corruption is prevent data corruption is bit paritybit parity. . Take a stream of binary, add up the Take a stream of binary, add up the
numbers, you get an odd or an even numbers, you get an odd or an even number. number.
Add a digit at the end of the data to Add a digit at the end of the data to indicate if the sum is odd or even. indicate if the sum is odd or even.
The receiving computer compares the The receiving computer compares the sum of the data stream to the bit parity sum of the data stream to the bit parity digit. digit.
Error DetectionError Detection

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
Information travels between Information travels between computerscomputers
in a network in one of three ways: in a network in one of three ways: Simplex transmissionSimplex transmission – information – information
travels in one direction only travels in one direction only Half-duplexHalf-duplex – information travels in – information travels in
both directions, one way at a timeboth directions, one way at a time Full duplexFull duplex – data is transmitted in – data is transmitted in
both directions simultaneouslyboth directions simultaneously
Data TransmissionData Transmission

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
Designing a NetworkDesigning a Network
Look at three things: Look at three things: The The fastest throughput and fastest throughput and
responseresponse time possible time possible The The least-cost pathleast-cost path – the data – the data
flows through the fewest devices flows through the fewest devices possiblepossible
Design reliabilityDesign reliability

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
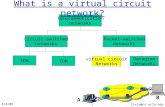
Things That ConnectThings That Connect
Networks accomplish data transfer Networks accomplish data transfer with awith a
concept called concept called packet switchingpacket switching. . Unused (available) portions of a Unused (available) portions of a
network are chosen network are chosen Data passes through the most Data passes through the most
efficient available means efficient available means

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
In networks, the connection point In networks, the connection point between your computer and the between your computer and the network is commonly a network is commonly a modemmodem. .
Modems have become Modems have become asymmetric asymmetric digital subscriber line (ADSL).digital subscriber line (ADSL). The word The word asymmetrical is used because these asymmetrical is used because these modems send data faster in one modems send data faster in one direction than the other. direction than the other.
Things That ConnectThings That Connect

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
Most homes and offices have a dedicated copperMost homes and offices have a dedicated copperwire running between them and the telephonewire running between them and the telephonecompany’s central office. company’s central office. The copper wire can carry far more data than The copper wire can carry far more data than
the 3,000 Hz signal of a typical telephone the 3,000 Hz signal of a typical telephone conversation conversation
The copper wire can act as a purely digital high-The copper wire can act as a purely digital high-speed transmission channel (1 million bps). speed transmission channel (1 million bps).
The same line can transmit both a telephone The same line can transmit both a telephone conversation and the digital data. conversation and the digital data.
Asymmetric Digital Subscriber Asymmetric Digital Subscriber Line - Line - DSLDSL

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
Other waysOther ways of connecting to a network of connecting to a network
Use a Use a hubhub Most hubs include a Most hubs include a switchswitch. A . A
switch determines how data will switch determines how data will travel along its path to the intended travel along its path to the intended destination – to look for the optimal destination – to look for the optimal route route
A A routerrouter is like a switch. A router is is like a switch. A router is a bridge between two networks. a bridge between two networks. The router determines the best path The router determines the best path between two different networks between two different networks

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
A A remote switchremote switch is one that is at your is one that is at your location but controlled by someone location but controlled by someone else at different location. else at different location.
A A trunktrunk is a circuit between different is a circuit between different types of switching equipment. types of switching equipment.
MiddlewareMiddleware describes a software that describes a software that is used to connect different is used to connect different applications (the translator). applications (the translator).
Network TermsNetwork Terms

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
Data CompressionData Compression
Techniques to Techniques to reduce the size of reduce the size of data in order to data in order to improve storage improve storage and bandwidth and bandwidth (transmission) (transmission) capacity.capacity.

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
BandwidthBandwidth Refers to the Refers to the capacitycapacity of of
the medium that carries the medium that carries the signal. the signal.
Analog bandwidth is Analog bandwidth is measured in Hz. measured in Hz.
Digital bandwidth is Digital bandwidth is measured in the measured in the number of bits per number of bits per second the medium can second the medium can carry. carry.
Determines the speed Determines the speed at which data can be at which data can be moved through a moved through a networknetwork
More bandwidth = more data, faster

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
ProtocolsProtocols
An agreement between people on An agreement between people on how a transaction should take how a transaction should take place. place.
Many networks use the Many networks use the Transmission Control Transmission Control Protocol/Internet Protocol (TCP/IP).Protocol/Internet Protocol (TCP/IP). Your computer must use TCP/IP to Your computer must use TCP/IP to go on the Internet. go on the Internet.

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
Basic Network TypesBasic Network Types
HierarchicalHierarchical - vertical - vertical or tree structureor tree structure
Local Area Network Local Area Network (LAN(LAN) - horizontal ) - horizontal network. Allows each network. Allows each device on the network device on the network to receive every to receive every network transmission. network transmission.
Star ConfigurationStar Configuration – All – All transmissions come transmissions come from a hub.from a hub.

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
LANLAN is a network that operates in is a network that operates in oneone specific location. specific location.
Wide Area Network (WAN)Wide Area Network (WAN) is is used to connect geographically used to connect geographically separated networks together. separated networks together.
Basic Network TypesBasic Network Types

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
Basic Network TypesBasic Network Types
Wireless Local Wireless Local Area Network Area Network (WLAN)(WLAN) uses radio uses radio waves to connect waves to connect among the mobile among the mobile node, mobile node, mobile computer, and computer, and the hardwired the hardwired network.network.

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
Data SecurityData Security
Could be called Network security Could be called Network security or Computer security. or Computer security.
What we are most trying to What we are most trying to protect is the informationprotect is the information contained in the various contained in the various systems. systems.

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
Physical Security is . . . Physical Security is . . .
Anything we do to physically Anything we do to physically protectprotect
our systems and information:our systems and information: Placing servers, routers and Placing servers, routers and
switching equipment behind switching equipment behind locked doorslocked doors
Backing up data in one or more Backing up data in one or more location location

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
FirewallFirewall - operates by controlling - operates by controlling access to the network based upon access to the network based upon the contents of the data packets the contents of the data packets being transmitted on the network. being transmitted on the network.
EncryptionEncryption - changing text or data - changing text or data into a form that is unreadable into a form that is unreadable without a key (secret code) without a key (secret code)
Virtual Security is…..Virtual Security is…..

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
Virtual Security is…..Virtual Security is…..
Intrusion DetectionIntrusion Detection – – security management security management system that gathers system that gathers and analyses info and analyses info from different part of from different part of the network. Scans the network. Scans network looking for network looking for user and system user and system activity and any activity and any pattern of abnormal pattern of abnormal behavior. behavior.

Copyright Protected 2005: Hi Tech Criminal Justice, Raymond E. Foster
Police TechnologyPolice Technology
Go to the Go to the Student ResourcesStudent Resources page page at at
www.hitechcj.comwww.hitechcj.com