HP 5920 & 5900 Switch Series Configuration · PDF file1 802.1X configuration examples This...
Transcript of HP 5920 & 5900 Switch Series Configuration · PDF file1 802.1X configuration examples This...
HP 5920 & 5900 Switch Series Configuration Examples
Copyright 2014 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice. The only warranties for HP products and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein.
Part number: 5998 5574
i
Contents
802.1X configuration examples 1
AAA configuration examples 19
ACL configuration examples 34
ARP attack protection configuration examples 58
ARP configuration examples 67
Proxy ARP configuration examples 71
BGP configuration examples 77
CFD configuration examples 93
DHCP configuration examples 101
DLDP configuration examples 114
DNS configuration examples 124
Emergency Shell Usage Examples 137
Ethernet OAM configuration examples 141
FCoE configuration examples 144
FIPS configuration examples 234
IGMP configuration examples 240
IGMP snooping configuration example 245
Information center configuration examples 253
IP addressing configuration examples 260
IP performance optimization configuration examples 263
IP source guard configuration examples 268
IPsec configuration examples 274
IPv6 basics configuration examples 289
IPv6 multicast forwarding over a GRE tunnel configuration examples 293
IPv6 PIM configuration examples 299
IRF configuration examples 325
IS-IS configuration examples 370
ISSU examples 384
Link aggregation configuration examples 405
LLDP configuration examples 414
Login management configuration examples 418
Loop detection configuration examples 430
ii
MAC address table configuration examples 434
MAC authentication configuration examples 440
MCE configuration examples 451
Mirroring configuration examples 473
MLD configuration examples 497
MLD snooping configuration examples 502
NQA configuration examples 510
NTP configuration examples 515
OSPF configuration examples 543
Password control configuration examples 556
PIM configuration examples 561
Port isolation configuration examples 586
Port security configuration examples 592
Traffic policing configuration examples 606
GTS and rate limiting configuration examples 630
Priority and queue scheduling configuration examples 635
Configuration examples for implementing HQoS through marking local QoS IDs 649
RBAC-based login user privilege configuration examples 655
Appendix Configuring authentication modes for login users 720
sFlow configuration examples 730
SNMP configuration examples 734
Software upgrade configuration examples 741
Spanning tree configuration examples 753
SSH configuration examples 777
Static multicast route configuration examples 805
Task scheduling configuration examples 820
TRILL configuration examples 825
Tunneling configuration examples 836
UDP helper configuration examples 863
uRPF configuration examples 866
VLAN configuration examples 868
VLAN tagging configuration examples 873
IPv4-based VRRP configuration examples 921
IPv6-based VRRP configuration examples 972
1
802.1X configuration examples This chapter provides examples for configuring 802.1X authentication to control network access of LAN users.
Example: Configuring RADIUS-based 802.1X authentication (non-IMC server)
Applicable product matrix
Product series Software version
HP 5920
HP 5900
Release 2208P01
Release 2210
Network requirements As shown in Figure 1, users must pass 802.1X authentication to access the Internet. They use the HP iNode client to initiate 802.1X authentication.
Switch A uses a RADIUS server (Switch B) to perform RADIUS-based 802.1X authentication and authorization. The RADIUS server is an HP 5500 HI switch that runs Comware V5 software image.
Configure Ten-GigabitEthernet 1/0/1 to implement MAC-based access control so each user is separately authenticated. When a user logs off, no other online users are affected.
Figure 1 Network diagram
Configuration restrictions and guidelines When you configure RADIUS-based 802.1X authentication, follow these restrictions and guidelines:
Specify the authentication port as 1645 in the RADIUS scheme on the access device when an HP device functions as the RADIUS authentication server.
Enable 802.1X globally only after you have configured the authentication-related parameters. Otherwise, users might fail to pass 802.1X authentication.
2
The 802.1X configuration takes effect on a port only after you enable 802.1X globally and on the port.
Configuration procedures Configuring IP addresses
# Assign an IP address to each interface, as shown in Figure 1. Make sure the client, Switch A, and the RADIUS server can reach each other. (Details not shown.)
Configuring Switch A
1. Configure the RADIUS scheme:
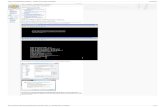
# Create RADIUS scheme radius1, and enter RADIUS scheme view. [SwitchA] radius scheme radius1
New Radius scheme
# Specify the RADIUS server at 10.1.1.1 as the primary authentication server. Set the authentication port to 1645. Specify the shared key as abc. [SwitchA-radius-radius1] primary authentication 10.1.1.1 1645 key simple abc
# Exclude the ISP domain name from the username sent to the RADIUS server. [SwitchA-radius-radius1] user-name-format without-domain
NOTE:
The access device must use the same username format as the RADIUS server. For example, if the RADIUS server includes the ISP domain name in the username, the access device must also include the ISP domain name.
# Set the source IP address for outgoing RADIUS packets to 10.1.1.2. [SwitchA-radius-radius1] nas-ip 10.1.1.2
[SwitchA-radius-radius1] quit
2. Configure the ISP domain:
# Create ISP domain test, and enter ISP domain view. [SwitchA] domain test
# Configure ISP domain test to use RADIUS scheme radius1 for authentication and authorization of all LAN users. [SwitchA-isp-test] authentication lan-access radius-scheme radius1
[SwitchA-isp-test] authorization lan-access radius-scheme radius1
[SwitchA-isp-test] quit
# Specify domain test as the default ISP domain. If a user does not provide any ISP domain name, it is assigned to the default ISP domain. [SwitchA] domain default enable test
3. Configure 802.1X:
# Enable 802.1X on port Ten-GigabitEthernet 1/0/1. [SwitchA] interface ten-gigabitethernet 1/0/1
[SwitchA-Ten-GigabitEthernet1/0/1] dot1x
# Configure Ten-GigabitEthernet 1/0/1 to implement MAC-based access control. By default, the port implements MAC-based access control. [SwitchA-Ten-GigabitEthernet1/0/1] dot1x port-method macbased
3
[SwitchA-Ten-GigabitEthernet1/0/1] quit
# Enable 802.1X globally. [SwitchA] dot1x
Configuring the RADIUS server
# Create RADIUS user guest, and enter RADIUS server user view. system-view
[Sysname] radius-server user guest
# Set the password to 123456 in plain text for RADIUS user guest. [Sysname-rdsuser-guest] password simple 123456
[Sysname-rdsuser-guest] quit
# Specify RADIUS client 10.1.1.2, and set the shared key to abc in plain text. [Sysname] radius-server client-ip 10.1.1.2 key simple abc
Configuring the 802.1X client
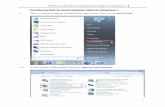
1. Open the iNode client as shown in Figure 2.
Figure 2 Opening the iNode client
2. Click New.
3. On the Create New Connection Wizard window, select 802.1X protocol, and then click Next.
4
Figure 3 Creating a new connection
4. Configure the connection name, username, and password, and then click Next.
5
Figure 4 Configuring the connection name, username, and password
For authentication to be performed correctly, the following details must comply with the correlation rules shown in Table 1:
Username specified on the iNode client.
Domain and username format configuration on the access device.
Service suffix on UAM.
Table 1 Parameter correlation
Username format on the iNode client
Domain on the access device
Username format configured on the access device
Service suffix on UAM
X@Y Y with-domain Y
X@Y Y without-domain No suffix
X Default domain
(the default domain specified on the access device)
with-domain Name of the
default domain
X Default domain
(the default domain specified on the access device)
without-domain No suffix
5. Configure the network property settings.
6
If you set local authentication as the backup authentication method, do not select Carry version info(J) in the User Options area. The access device cannot recognize the version number carried in EAP packets.
Figure 5 Configuring 802.1X connection properties
6. Click Create.
7
Figure 6 Completing the new connection wizard
Verifying the configuration Verify that you can use the user account to pass 802.1X authentication:
# Double-click My 802.1X Connection on the iNode client.
# On the My 802.1X Connection window, enter username guest@test and password 123456.
# Click Connect.
8
Figure