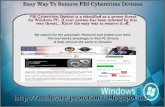
Uninstall fbi cybercrime division:how to uninstall fbi cybercrime division
Cybercrime 3
-
Upload
marcus-wilson -
Category
Documents
-
view
38 -
download
2
Transcript of Cybercrime 3

Cybercrime and other forms of malfeasance are responsible for a slew of industry and government rules and regulations that law-abiding citizens must endure … and pay for.
Acronyms abound: PCI-DSS, HIPAA/HITECH, GLBA and ISO 27001 are but a few. Not to be mistaken as o�spring triplets of SOX are SOC 1, SOC 2 and SOC 3 reports defined under SSAE-16 and AT-101. The intention behind these requirements is for the greater good, not the least of which are protecting people from exploitation and stopping crime. Besides, resistance is futile. So, you might as well look on the bright side. Here are some ways that compliance is actually good for business operations and management, whether your IT operations are on premise or cloud hosted.
Cybercrime and other forms of malfeasance are responsible for a slew of industry and government rules and regulations that law-abiding citizens must endure … and pay for.
Acronyms abound: PCI-DSS, HIPAA/HITECH, GLBA and ISO 27001 are but a few. Not to be mistaken as o�spring triplets of SOX are SOC 1, SOC 2 and SOC 3 reports defined under SSAE-16 and AT-101. The intention behind these requirements is for the greater good, not the least of which are protecting people from exploitation and stopping crime. Besides, resistance is futile. So, you might as well look on the bright side. Here are some ways that compliance is actually good for business operations and management, whether your IT operations are on premise or cloud hosted.