Color Scheme Authentication
Transcript of Color Scheme Authentication
-
7/21/2019 Color Scheme Authentication
1/25
MINI PROJECT 2014
Color Scheme Authentication
OPERATIONAL FEASIBILITY
The proposed system was found to feasible in all these different classifications of
the study and this led to the design of the system.
The important points to be studied before the design of the system are the software
engineering principles such as:
Rigor and formality
Separation of concerns
Modularity
Abstraction Anticipation of change
Generality
Incrementality
The above principles were carefully studied and implemented in various phases of
the proect! which will be discussed in the following sections.
Rigor and formality: Software "ngineering is a creative design activity! but it
must be practiced systematically. Rigor is a necessary complement to
creativity that increases our confidence in our developments. #ormality is
rigor at the highest degree. Rigorous documentation of development steps
helped proect management and assessment of timeliness.
Separation of concerns: To dominate comple$ity! separate the issue to
concentrate on one at a time. %&ivide ' con(uer) supports paralleli*ation of
efforts and separation of responsibilities. Go through phases one after the
other+as in water fall model,. -e did separation of concerns by separating
activities with respect to parts. This resulted in two parts of the proect which
made the tas (uite simple.
Modularity: A comple$ system may be divided into simpler pieces called
modules. A system that is composed of modules is called modular. The
concepts of cohesion and coupling are to be applied. -hen dealing with a
-
7/21/2019 Color Scheme Authentication
2/25
module we can ignore details of other modules. There are two modules in this
proect which handles server and client.
Abstraction: Identify the important aspects of a phenomenon and ignore its
details. It is a special case of separation of concerns. The type of abstraction
to apply depends on its purpose. #or e$ample: The comple$ity of
authentication process is hidden from the user.
Anticipation of change: Ability to support software evolution re(uires
anticipating potential future changes. It is the basis for software evolvability.
#or e$ample: #urther versions of encryption algorithm can easily be
implemented in the proposed system.
Generality: The principle of generality is closely related to the principle of
anticipation of change. It is important in designing software that is free from
unnatural restrictions and limitations. -hile solving a problem! try to discover
if it is an instance of a more general problem whose solution can be reused in
other cases. /arefully! balance generality against performance and cost!
sometimes a general problem is easier to solve than a special case. 0ur
system is more generalised to all classes of biometric data sets which
includes face recognition! iris! hand geometry etc.
Incrementality: An incremental software development process simplifiesverification. If you develop software by adding small increments of
functionality then! for verification! you only need to deal with the added
portion. If there are any errors detected then they are already partly isolated
so they are much easier to correct. A carefully planned incremental
development process can also ease the handling of changes in re(uirements.
To do this! the planning must identify use cases that are most liely to be
changed and put them towards the end of the development.process.
SYSTEM DESIGN AND ANALYSIS
INPUT DESIGN
-
7/21/2019 Color Scheme Authentication
3/25
MINI PROJECT 2014
The input design is very important for any application. The input design describes
how the software communicates within itself! to system that interested with it and with
human who use it. The input design is the process of converting the user1oriented
inputs into the computer1based format. The data is fed into the system using simple
interactive forms. The forms have been supplied with message so that user can enter
the data without facing any difficulty. The data is validated wherever it re(uires in the
proect.
OUTPUT DESIGN
0utputs are the most important and direct source in information to the consumer
and administrator. Intelligent output design will improve the system2s relationship with
user and help in decision maing. It has a conversation panel to display the connection
information! remote messages and information for user.
"fficient! intelligent output design should improve the system2s relationship with
the user and help in decisions maing. Since the reports are directing reffered by the
management for taing decision and to draw conclusion they must be designed with
almost care and the details in the reports must be simple! descriptive and clear to the
user. So while designing output the following things are to be considered.
EISTING SYSTEM
Traditonal method used for authentication is te$tual password. The
volunerabilities of this method lie eves dropping!dictionary attac! social enginnering
and shoulder suffering are well nown. Random and lengthy passwords can mae the
system secure. 3ut the main problem is the difficulty of remembering those passwords.
Studies have shown that users tend to pic short passwords or passwords that are easy
to remember. 4nfortunately! these passwords can be easily guessed or craced.
PROPOSED SYSTEM
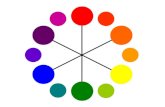
-e propose a new authentication scheme %/olor Scheme Authentication ).
Instead of ust words we propose a system in which authentication is done using colors
and numbers. 4sers can give values from 5 to 6 for the given 6 colors. 4sres can even
-
7/21/2019 Color Scheme Authentication
4/25
give same value for two different colors.this maes the authentication method ris free
of shoulder attac! dictionary attac!eves dropping etc. That is evolved if the logic every
user uses for giving values for colors is simple.
&uring registration! user should rate colors. The user should rate colors from 5 to
6and he can remember it as %R7803GI9). Same rating can given to different colors.
&uring the login phase! when the user enters his user name an interface is displayed
based on the colors selected by the user. The login interphase consists of grid of si*e
6$6. This contains digit 516 placed randomly in grid cells. The interface also contains
strips of colors. The color grid consists of pairs of colors. "ach pair of color represents
the row and the colomn of the grid.
-
7/21/2019 Color Scheme Authentication
5/25
MINI PROJECT 2014
-
7/21/2019 Color Scheme Authentication
6/25
The login interface having the color grid and number grid of 6$6 having numbers
5 to 6 randomly placed in the grid. &epending on the ratings given to colors! we get the
session passwords. As discussed above! the first color of every pair in color grid
represents row and second represents colomn of the number grid. The number in the
intersection of the row and colomn of the grid is part of the session password. The first
pair has red and yellow colors. The red color rating is 5 and yellow color rating is ;. So
the first letter of session password is 5strow and ;rdcolomn intersecting element i.e! ;.
The same method is followed for other pairs of colors. So the password is %;char+MA?, uncheced
4name >char+MA?, 4ncheced
Sec( >char+MA?, 4ncheced
Ans >char+MA?, 4ncheced
"id >char+MA?, 4ncheced
9hno >char+MA?, 4ncheced
7ac >char+MA?, 4ncheced
3lue >char+MA?, 4ncheced
Red >char+MA?, 4ncheced
0range >char+MA?, 4ncheced
8ellow >char+MA?, 4nchecedGreen >char+MA?, 4ncheced
3rown >char+MA?, 4ncheced
>iolet >char+MA?, 4ncheced
-
7/21/2019 Color Scheme Authentication
7/25
MINI PROJECT 2014
SYSTEM RE!UIREMENTS
"ar#$are Re%uirement&
9rocessor : Intel or AM& processor computer RAM : @
-
7/21/2019 Color Scheme Authentication
8/25
interface designers!integrated debugger!and many other tools to mae it easier to
develop applications based on version .D of the cE language and version .D of the
.Cet framewor.
ASP)NET 'rame $or*
The .Cet languages: these include visual basic! cE! script . Cet ! E and c.
The /ommon7anguage Runtime +/7R,: this is the engine that e$ecutes
all .Cet programs and provides automatic services for these applications!such as
security checing!memory management! and optimi*ation.
The .Cet frame wor class library : the class library collects thousands
of pieces of prebuilt functionality that you can %snap in) to your applications.These
feature sare sometimes organised into technology sets ! such as A&0.C"T+the
technology for creating database applications,and windows forms+the technology for
creating destop user interfaces,.
AS9.C"T:this is the engine that hosts the web applications you create
with .Cet and supports almost any feature from the .Cet class library.AS9.C"T also
includes a set ofwebspecific services!lie secure authentication and data storage.
>isual studio :this optional development tool consists of a rich set of
productivity and system development life cycle +S&7/,models have been created:
waterfall!fountain!spiral!build and fi$!rapid prototyping!incremental and synchroni*edand stabilise.
BAC+ END
S!L Ser,er -../
Microsoft SF7server is a relational database server ! developed by
Microsoft : it is a software product whose primary function is to store and retrieve data
as re(uested by other software applications !be it those on the same computer or those
running onanother computer across anetwor.There are atleast a do*en different
editions of Microsoft SF7server aimed at different audiences and for different worloads
+ranging from small applications that store and retrieve data on the same computer!to
millions of users and computers that access hugeamounts of data from the internet at
the same time,.
-
7/21/2019 Color Scheme Authentication
9/25
MINI PROJECT 2014
SF7server @DD6 was released on august !@DD6 and aims to mae data
management self turing !self organi*ing !and self maintaining with the development of
SF7 server alwaya on technologies!to provide near *ero down time.SF7sever @DD6
also includes support for structured and semi structured data. Microsoft!SF7server
@DD6 can be a data storage bac end for different varieties of data :
$ml!email!timeHcalendar!file!document!spatial etc as well as perform search !(uery
!analysis!sharing and synchroni*ation across all data types
IMPLEMENTATION
Implementation is the stage of the proect when the theoretical design is turned
into a woring system. This is the final and important phase in the life cycle. It is actually
a process of converting a new system into an operational one.
Ta&* o' im0lementation
It is a process of bringing a developed system into components which are to be
tested ina structured and planned manner. The software should be delivered to the
users and they should have confidence that the system wor efficiently and effectively!
The more comple$ the system being implemented the more involved will be the
system analysis and design efforts re(uired for implementation.
The system carrying three modules has been implemented with confirmed
effectiveness!detection and correction of errors and maing necessary all decisions on
their true or false side changes so as to satisfy the re(uirements.
The system is using very few software pacages lie .Cet and it use the bac end
as SF7.This will very useful to store the information of the user and also easily can
transmit the data to the other user securely. This is the main advantage of the system.
-ith the system is implementing the resources can be get in very low cost.
Front En# Im0lementation
-e have designed the front end using .Cet framewor version .D. It is user
friendly and easy to use. the necessary forms re(uested for the proect could easily be
built with this. -e have created three forms in the user side. -e have drag and drop
options for placing necessary buttons on the form. There are many inbuilt pacages
-
7/21/2019 Color Scheme Authentication
10/25
visual studio to mae the design phase attaractive we ust have to import them to the
program code. since for performing all these activities we use visual studio @D5D..Cet is
the suited language for implementing our proect.
Mo#ule ,ice Im0lementation
Mainly we have @ main modules in our proect
Admin Module
4ser Module
A#min Mo#ule&
"ncryption
Authentication
Randomi*ation
U&er Mo#ule&
Sign up
7og in
Recovery
A#min mo#ule im0lementation
It consists of "ncryption! Authentication and Randomi*ation. These are done on
the coding part.
#unction for encryption is given
PublicstringEncrypt (stringplaintext, stringkey) {
byte[] clearBytes =
System.Text.Enc!ing."nic!e.#etBytes(plainText)$
-
7/21/2019 Color Scheme Authentication
11/25
MINI PROJECT 2014
Pass%r!&eri'eBytesp!b = ne%Pass%r!&eri'eBytes(key, ne%
byte[] { x*, x+, x-, xe, x, x!, x/, x, x+, x/,
x, x/, x+ 0)$
byte[] encrypte!&ata = Encrypt(clearBytes, p!b.#etBytes(1),
p!b.#etBytes(-))$
return2n'ert.TBaseString(encrypte!&ata)$
0
Publicstaticbyte[] Encrypt(byte[] clear&ata, byte[] key, byte[]
34)
{
5emryStreamms = ne%5emryStream()$
6i7n!aelalg = 6i7n!ael.2reate()$
alg.8ey = key$
alg.34 = 34$
2ryptStreamcs = ne%2ryptStream(ms, alg.2reateEncryptr(),
2ryptStream5!e.9rite)$
cs.9rite(clear&ata, , clear&ata.:engt;)$
cs.2lse()$
byte[] encrypte!&ata = ms.T
-
7/21/2019 Color Scheme Authentication
12/25
Encr10tion al2orithm
Ri3n#ael4& Al2orithm
Rindael +pronounced rain1dahl, is the algorithm that has been selected
by the 4.S. Cational Institute of Standards and Technology +CIST, as the candidate for
the Advanced "ncryption Standard +A"S,. It was selected from a list of five finalists! that
were themselves selected from an original list of more than 5< submissions. Rindael
will begin to supplant the &ata "ncryption Standard +&"S, 1 and later Triple &"S 1 over
the ne$t few years in many cryptography applications. The algorithm was designed by
two 3elgian cryptologists! >incent Rimen and Joan &aemen! whose surnames arereflected in the cipherKs name. Rindael has its origins in S(uare! an earlier collaboration
between the two cryptologists.
The Rindael algorithm is a new generation symmetric bloc cipher that supports ey
si*es of 5@6! 5L@ and @
-
7/21/2019 Color Scheme Authentication
13/25
-
7/21/2019 Color Scheme Authentication
14/25
;,AddRoundey
The Su9B1te& &te0
In the Sub3ytesstep! each byte in the state is replaced with its entry in a fi$ed 61bit
looup table! S bijO S(aij).
In the Sub3ytes step! each byte in the matri$ is updated using an 61bit substitution bo$!
the Rindael S1bo$. This operation provides the non1linearity in the cipher. The S1bo$ used is
derived from the multiplicative inverse over GF+28,! nown to have good non1linearity properties.
To avoid attacs based on simple algebraic properties! the S1bo$ is constructed by combining
the inverse function with an invertible affine transformation. The S1bo$ is also chosen to avoid
any fi$ed points +and so is a derangement,! and also any opposite fi$ed points.
The Shi't Ro$& &te0
-
7/21/2019 Color Scheme Authentication
15/25
MINI PROJECT 2014
In the ShiftRows step! bytes in each row of the state are shifted cyclically to the left.
The number of places each byte is shifted differs for each row.
The ShiftRows step operates on the rows of the state it cyclically shifts the bytes in
each row by a certain offset. #or A"S! the first row is left unchanged. "ach byte of the
second row is shifted one to the left. Similarly! the third and fourth rows are shifted by
offsets of two and three respectively. #or the bloc of si*e 5@6 bits and 5L@ bits the
shifting pattern is the same. In this way! each column of the output state of the
ShiftRows step is composed of bytes from each column of the input state. +Rindael
variants with a larger
bloc si*e have slightly different offsets,. In the case of the @
-
7/21/2019 Color Scheme Authentication
16/25
&uring this operation! each column is multiplied by the nown matri$ that for the 5@6 bit
ey.
The multiplication operation is defined as: multiplication by 5 means
leaving unchanged! multiplication by @ means shifting byte to the left and multiplication
by ; means shifting to the left and then performing $or with the initial unshifted value.
After shifting! a conditional $or with D$53 should be performed if the shifted value is
larger than D$##.
In more general sense! each column is treated as a polynomial over
G#+@6, and is then multiplied modulo $5 with a fi$ed polynomial c+$, O D$D; P $; $@
$ D$D@. The coefficients are displayed in their he$adecimal e(uivalent of the binary
representation of bit polynomials from G#+@,Q$. The Mi$/olumns step can also be
viewed as a multiplication by a particular M&S matri$ in a finite field. This process is
described further in the article Rindael mi$ columns.
The A##Roun#+e1 &te0
-
7/21/2019 Color Scheme Authentication
17/25
MINI PROJECT 2014
In the AddRoundey step! each byte of the state is combined with a byte of the round
subey using the ?0R operation +,. In the AddRoundey step! the subey is combined
with the state. #or each round! a subey is derived from the main ey using RindaelKs
ey schedule each subey is the same si*e as the state. The subey is added by
combining each byte of the state with the corresponding byte of the subey using
bitwise ?0R.
U&er mo#ule im0lementation
4ser module consists of ; modules
Sign up
7og in
Recovery
Si2n u0
Sign up module is the main part of the proect. This module is used to sign up color
scheme authentication. The signup includes username! email id! security (uestion and
answer along with password. 4nless user don2t sign up user cannot login.
Lo2in
The login module is nothing but the processes of logging of a signed up user usingcolor scheme authentication. The user has to login using color scheme authentication
to get to his account.
Reco,er1
The Recovery module does the recovery of the user account in case user forgets the
password. This is done by using a custom security (uestion and answer. 0nce the user
passes this process he will be redirect to page from which the user can get bac
access to his account.
TESTING
Testing is the vital to the success of the system.System itesting maes a logical
assumption that if all the part of the system are correct!the goal will be successfully
-
7/21/2019 Color Scheme Authentication
18/25
achieved.System testing is the stage of implementation that we aimed at assuring that
the system wors accurately and efficiently before live operation commences.
Software testing is a critical element of software (u(lity assurance represents the
ultimate review of specification!design and coding.The user tests the developed system
and changes are made according to there needs.The testing phase involves the testing
of developed system using various inds of data.
Te&tin2 O93ecti,e&
Testing is the process of e$ecuting the program with the intention of
finding an error
A good test is one that has high probability of finding an as yet
undiscovered
A successful test is that which uncovers as1yet1undiscovered error
;hite 9o: te&tin2
-hite bo$ testing foccuses on the program control structure.In our proect whenuser enters his details!thesystem will chec the database and if it is valid then the whole
lines are from.And also when the message to the user the whole lines are reading from
the te$t area and it will display in the same format in the receiver side.These are all
indicates that the control structures wor efficiently. If there is any error it will display the
null pointer e$cepion in the console.
Blac* 9o: te&tin2
3lac bo$ testing is a method of software testing that tests the functionality of
application as opposed to its internal structures of worings+see white bo$
testing,.Specific nowledge of application2s codeHinternal structure and programming
nowledge in general is not re(uired.The tester is only aware of what the software is
supposed to do!but not how i.e.-hen he enters a certain input!he gets a crtain output
without being aware of how the output was produced in the first place.Test cases are
-
7/21/2019 Color Scheme Authentication
19/25
MINI PROJECT 2014
built around specifications and re(uirements!i.e.what the application is supposed to do.It
uses e$ternal descriptions of the software!including specifications!re(uirements!and
design to derive test cases.These tests can be functional or non1functional!though
usually functional.The designers selects valid and invalid inputs and determines the
correct output.There is no nowledge of the test obect2s internal structure.
Unit te&tin2
4nit testing is carried out to screen wise!each screen being identified as an
obect.Attention is diverted to individual modules! independently to one another to locate
errors in coding and logic
In unit testing
Module is tested to ensure that information properly flows into and
out of the program uder test.
7ocal data structures are e$amined to ensure that data stored
temporarily maintains its integrity during all steps in algorithm
e$ecution
3oundary condition is tested to ensure that module operates
properly at boundaries established to limit or restrict processing.
All independent paths through the control structures are e$ecuted
to ensure that all atatements in the module have been e$ecuted atleast once.
"rror handling paths are also tested.this tests focuses verification
effort on the smallest unit of software design modules.
Bere the module interfacs boundary conditions and all indipendent paths were
verified by inputting false data."ach single operation is tested individually for its correct
functionality.
Inte2ration te&tin2
Integration testing is a systematic techni(ue for constructing the program
structure while at the same time conducting tests to uncover errors asssociated with
interfacing.
-
7/21/2019 Color Scheme Authentication
20/25
4nit tested module were taen and single program structure was built that has been
dictated by the design.Incremental integration has adpoted here.The entire software
was developed and tested in small segments where errors were easily to locate and
rectify."ach database or table manipulation operation were separately tested and
combined to form a single program.After integation!the single program was tested again
with numerous test data to chec for its functionality.
The integration can be performed in two ways Top &own integration and 3ottom
4p integration
Al0ha te&tin2
A series of acceptance tests were conducted to enable the employees of the firm
to validate re(uirements.The end user conducted it.The suggestions!along with the
additional re(uirements of the end user were included in the proect.
Beta te&tin2
It is to be conducted by the end1user without the presence of the developer.It can
be conducted over a period of wees or month.Since it is a long time consuming
activity!it result is out of scope of this proect report.3ut its result will help to enhance the
product at later time.
Final te&tin2
-hen a system is developed! it is hoped that it performs properly.In practice!
however ! some errors always occur.The main purpose of testing an information system
is to find the errors and correct them.A successful test is one! which finds an error.
APPENDI A
-
7/21/2019 Color Scheme Authentication
21/25
MINI PROJECT 2014
USER MANUAL
1. Install .net and SF7 Server.
2. /reate database and tables on SF7 Server.
3. Run the program code on the visual studio.
4. /reate a new account as shown in figure.
5. A registered user can directly login by typing hisHher username and password as
shown in figure.
6. If verification is success then! heHshe can enter.
7. If the user lost his password they can retrieve it from the password recovery by
using security (uestion.
APPENDI B
SCREEN S"OTS
-
7/21/2019 Color Scheme Authentication
22/25
Fig 1 Sign up
-
7/21/2019 Color Scheme Authentication
23/25
MINI PROJECT 2014
Fig 2 Login
-
7/21/2019 Color Scheme Authentication
24/25
Fig 3 Passo!" R#$o%#!&
-
7/21/2019 Color Scheme Authentication
25/25
MINI PROJECT 2014
Fig 4 '#(au)*